In today’s interconnected world, the importance of security in embedded devices cannot be overstated. These devices, which power a wide range of applications from smart home appliances to industrial automation, are becoming increasingly sophisticated and complex. As a result, they are also becoming more vulnerable to security threats. In this blog, we will explore the common security challenges faced by embedded systems and discuss strategies for ensuring end-to-end security in these devices.
Embedded systems are integral to our daily lives, making our world smarter, more efficient, and more connected. However, this increased connectivity also exposes embedded devices to numerous security risks, compromising the integrity and confidentiality of the data they process and store. Addressing these risks is crucial to maintaining the trust of users and safeguarding the overall security of the systems they interact with.
Throughout this blog, we will delve into the landscape of embedded systems, the security risks and vulnerabilities associated with these devices, and the key components of end-to-end security. We will also share best practices for designing and implementing secure embedded devices, and provide a case study illustrating the successful implementation of end-to-end security in a real-world setting. Our goal is to equip you with the knowledge and insights needed to protect your embedded devices against emerging security threats and ensure the safety and privacy of your users.
Understanding the Embedded Systems Landscape
Before diving into the security aspects of embedded devices, it’s essential to understand what embedded systems are and the role they play in various industries. Let’s begin with a definition and examples of embedded systems.
Definition and Examples of Embedded Systems
An embedded system is a computer system designed to perform specific tasks with dedicated functions, typically within a larger system. These systems often have real-time constraints and are designed for efficiency and reliability. They can range from simple devices, such as digital watches, to complex systems, like avionics control systems in aircraft.
Examples of embedded systems include:
- Home appliances like washing machines and microwaves
- Automotive systems, such as engine control units and anti-lock braking systems
- Medical devices like pacemakers and insulin pumps
- Industrial automation equipment, including programmable logic controllers and robotics
- Consumer electronics, such as smartphones, cameras, and gaming consoles
The Role of Embedded Systems in Various Industries
Embedded systems play a crucial role across a wide range of industries, providing specialized functionality and enabling complex interactions between various components. In the automotive industry, for example, embedded systems control everything from engine performance to safety features, such as airbags and collision avoidance systems.
In healthcare, embedded devices like heart monitors and infusion pumps help monitor and manage patients’ conditions, while industrial automation systems streamline manufacturing processes and improve efficiency.
As a result, embedded systems have become indispensable in modern society, driving innovation and enhancing the performance, safety, and convenience of the products and services we rely on every day.
The Increasing Need for Secure Embedded Devices
As embedded systems become more pervasive and interconnected, the need for robust security measures to protect these devices from cyber threats has grown exponentially. Cybercriminals are increasingly targeting embedded systems to gain unauthorized access, disrupt operations, or compromise sensitive data. The consequences of such attacks can be catastrophic, leading to financial losses, reputational damage, and even physical harm.
Moreover, the increasing integration of embedded systems with cloud services and the Internet of Things (IoT) further amplifies the potential attack surface, making it imperative for organizations to prioritize security in the design and deployment of their embedded devices. By implementing robust end-to-end security measures, organizations can safeguard their embedded systems and protect their users’ privacy and safety.
Security Risks and Vulnerabilities in Embedded Devices
To effectively protect embedded devices from security threats, it’s crucial to understand the types of attacks they may face and the common vulnerabilities that can be exploited. In this section, we will discuss various security threats and attacks, followed by an overview of prevalent vulnerabilities in embedded systems.
Types of Security Threats and Attacks
Embedded devices can be targeted by various types of attacks, which can be broadly categorized into three groups: physical attacks, network attacks, and software attacks.
Physical Attacks
Physical attacks involve direct tampering with the hardware of an embedded device. These attacks can include actions like probing, reverse engineering, or modifying the device’s components to extract sensitive information or compromise its functionality. Physical attacks often require the attacker to have physical access to the device, making them more challenging to execute. However, when successful, these attacks can have severe consequences, including the theft of intellectual property or the disabling of critical systems.
Network Attacks
Network attacks target the communication channels used by embedded devices, aiming to intercept, modify, or disrupt the data transmitted between them. These attacks can be carried out remotely and can include eavesdropping, man-in-the-middle attacks, and denial-of-service attacks. Network attacks can lead to data breaches, unauthorized access to sensitive information, and the disruption of critical services.
Software Attacks
Software attacks exploit vulnerabilities in the firmware or software running on embedded devices. Examples of software attacks include buffer overflows, code injection, and privilege escalation. These attacks can be executed remotely or locally and can result in unauthorized access to the device, data theft, or disruption of its intended functionality.
Common Vulnerabilities in Embedded Systems
Several common vulnerabilities can make embedded systems susceptible to the attacks mentioned above. These vulnerabilities include weak encryption, inadequate access controls, and insufficient software updates.
Weak Encryption
Encryption is essential for protecting sensitive data and ensuring the confidentiality and integrity of communications between embedded devices. However, weak encryption algorithms or improper implementation can render encryption ineffective, leaving embedded systems vulnerable to attacks. Ensuring the use of strong encryption algorithms and proper key management practices is crucial for safeguarding embedded devices.
Inadequate Access Controls
Access controls help restrict unauthorized access to embedded devices and their sensitive data. However, inadequate access controls, such as weak passwords or poorly implemented authentication mechanisms, can be easily exploited by attackers. Implementing robust authentication and authorization mechanisms is essential to protect embedded devices from unauthorized access and potential data breaches.
Insufficient Software Updates
Regular software updates are critical for addressing security vulnerabilities and maintaining the overall security of embedded devices. However, many embedded systems lack efficient mechanisms for updating their firmware or software, leaving them exposed to known vulnerabilities. Ensuring timely and secure software updates is a vital component of maintaining a secure embedded system.
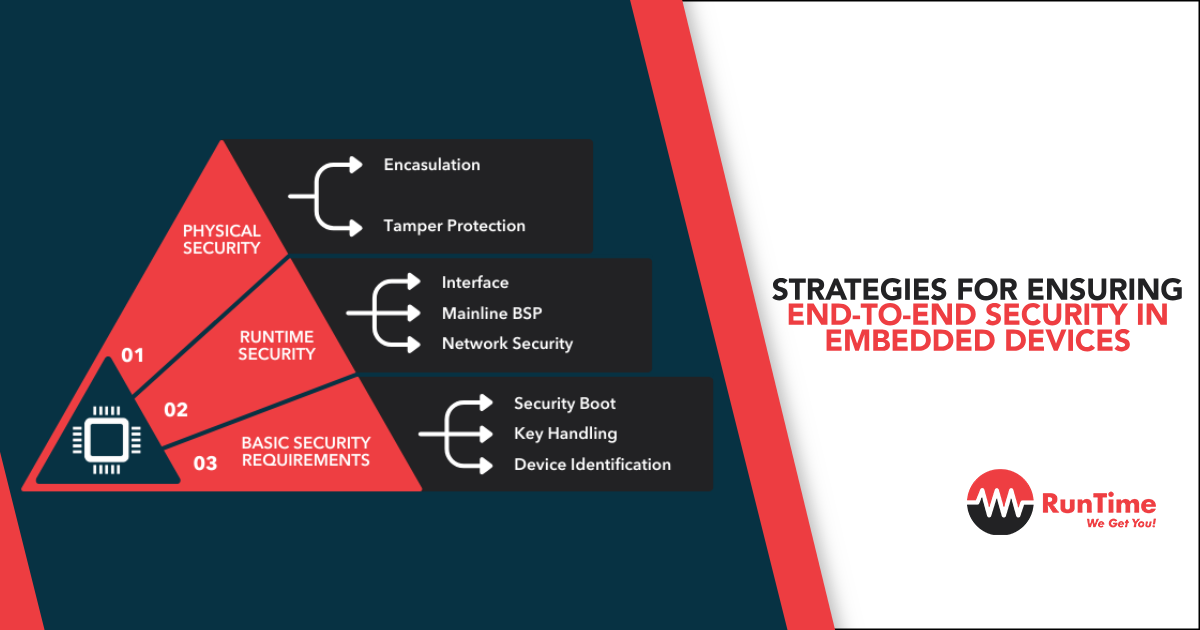
Key Components of End-to-End Security in Embedded Devices
Implementing end-to-end security in embedded devices requires a comprehensive approach that addresses various aspects of the device’s lifecycle, from design and development to deployment and maintenance. In this section, we will discuss the key components of end-to-end security in embedded devices, including secure boot processes, firmware updates, encryption, authentication, network security, and monitoring and auditing.
Secure Boot Process
A secure boot process ensures that an embedded device only runs trusted firmware and software, protecting it from unauthorized modifications and malicious code. This process typically involves verifying the digital signature of the firmware and software before execution, ensuring their authenticity and integrity. Implementing a secure boot process is essential for preventing tampering and maintaining the overall security of embedded devices.
Secure Firmware Updates
As mentioned earlier, regular firmware updates are critical for addressing security vulnerabilities and maintaining the overall security of embedded devices. Ensuring secure firmware updates involves verifying the authenticity and integrity of the updates, implementing secure communication channels for update delivery, and providing mechanisms for rollback in case of update failures. Secure firmware updates help protect embedded devices from potential security risks associated with outdated or compromised firmware.
Robust Encryption and Decryption
Encryption is essential for protecting sensitive data stored on embedded devices and ensuring the confidentiality and integrity of communications between them. Implementing robust encryption and decryption mechanisms involves using strong encryption algorithms, proper key management practices, and secure hardware and software components. Ensuring robust encryption and decryption is vital for safeguarding embedded devices against data breaches and unauthorized access.
Strong Authentication and Access Controls
Implementing strong authentication and access controls helps protect embedded devices from unauthorized access and potential data breaches. This includes using robust authentication mechanisms, such as two-factor authentication or digital certificates, and implementing proper authorization mechanisms to restrict access to sensitive data and functions. Ensuring strong authentication and access controls is crucial for maintaining the overall security of embedded devices.
Network and Communication Security
Protecting the communication channels used by embedded devices is essential for preventing network attacks and ensuring the confidentiality and integrity of data transmissions. Network and communication security involves implementing secure communication protocols, encrypting data transmissions, and using mechanisms like firewalls and intrusion detection systems to monitor and safeguard network connections. Ensuring network and communication security is critical for defending embedded devices against network-based attacks and potential data breaches.
Monitoring and Auditing
Continuous monitoring and auditing of embedded devices help identify potential security threats and vulnerabilities, enabling organizations to take proactive measures to protect their devices. This includes monitoring device logs, network activity, and system performance to detect anomalies, as well as conducting regular security assessments and audits to ensure compliance with industry standards and regulations. Implementing monitoring and auditing mechanisms is essential for maintaining the overall security of embedded devices and ensuring their continued protection against emerging threats.
Best Practices for Ensuring Security in Embedded Devices
Implementing end-to-end security in embedded devices requires a comprehensive and proactive approach. In this section, we will discuss several best practices for ensuring security in embedded devices, including adopting a security-first design approach, implementing multi-layered security strategies, regularly testing and updating security measures, ensuring compliance with industry standards and regulations, and collaborating with security experts and vendors.
Implementing a Security-First Design Approach
A security-first design approach involves prioritizing security considerations throughout the entire development lifecycle of embedded devices, from initial concept to final deployment. This includes incorporating security features from the earliest stages of design, continuously evaluating and addressing potential threats and vulnerabilities, and integrating security best practices into the development process. Adopting a security-first design approach helps minimize the potential attack surface and ensures the robustness of embedded devices against security threats.
Adopting a Multi-Layered Security Strategy
A multi-layered security strategy involves implementing multiple layers of protection to defend embedded devices against various types of attacks. This includes securing the hardware, software, and network components of the devices, as well as implementing robust encryption, authentication, and access control mechanisms. By adopting a multi-layered security strategy, organizations can enhance the overall security of their embedded devices and improve their resilience against potential attacks.
Regularly Testing and Updating Security Measures
Regular testing and updating of security measures are essential for maintaining the overall security of embedded devices. This includes conducting regular security assessments to identify potential vulnerabilities, updating firmware and software to address known security issues, and implementing the latest security best practices and technologies. Regularly testing and updating security measures help ensure the continued protection of embedded devices against emerging threats and vulnerabilities.
Ensuring Compliance with Industry Standards and Regulations
Compliance with industry standards and regulations is crucial for maintaining the security of embedded devices and reducing the risk of data breaches and other security incidents. This includes adhering to relevant security standards, such as ISO/IEC 27001 and NIST SP 800–53, as well as complying with industry-specific regulations like the Health Insurance Portability and Accountability Act (HIPAA) for healthcare devices and the Federal Information Security Management Act (FISMA) for government systems.
Ensuring compliance with industry standards and regulations helps organizations demonstrate their commitment to security and reduces the potential legal and financial risks associated with non-compliance.
Collaborating with Security Experts and Vendors
Collaborating with security experts and vendors can provide valuable insights and support in implementing end-to-end security for embedded devices. This includes seeking advice from security consultants, engaging with vendors that specialize in embedded security solutions, and participating in industry forums and events to stay informed about the latest security trends and best practices. Collaborating with security experts and vendors can help organizations improve the security of their embedded devices and better protect them against potential threats and vulnerabilities.
Case Study: Successful Implementation of End-to-End Security in Embedded Devices
To illustrate the importance of implementing end-to-end security in embedded devices, let’s take a look at a case study involving a company that successfully addressed its security challenges and enhanced the overall security of its embedded devices.
Overview of the Company and Its Embedded Devices
The company in question is a leading manufacturer of IoT-enabled smart home devices, including smart thermostats, security cameras, and lighting systems. These embedded devices communicate with each other and the cloud to provide users with seamless control over their home environment and enhance their overall comfort and security.
Security Challenges Faced by the Company
As the company’s IoT-enabled smart home devices gained popularity, they also attracted the attention of cybercriminals, exposing them to various security threats and attacks. The company faced several security challenges, including:
- Protecting sensitive user data stored on the devices
- Ensuring secure communication between the devices and the cloud
- Maintaining the integrity and authenticity of firmware updates
- Defending against unauthorized access and potential data breaches
Strategies and Solutions Implemented
To address these security challenges, the company implemented a comprehensive end-to-end security strategy that included the following measures:
- Adopting a security-first design approach that prioritized security considerations throughout the development lifecycle
- Implementing a multi-layered security strategy that secured the hardware, software, and network components of the devices
- Using robust encryption and decryption mechanisms to protect sensitive data and ensure the confidentiality and integrity of communications
- Employing strong authentication and access controls to restrict unauthorized access
- Establishing a secure firmware update process to address known security issues and maintain the overall security of the devices
- Collaborating with security experts and vendors to enhance the company’s security capabilities and stay informed about the latest security trends and best practices
Results and Benefits of the Secure Embedded Devices
As a result of implementing these security measures, the company was able to enhance the overall security of its embedded devices and protect them against various security threats and attacks. This had several positive outcomes, including:
- Reduced risk of data breaches and unauthorized access to sensitive user data
- Improved user trust and confidence in the company’s products
- Increased compliance with industry standards and regulations
- Enhanced the company’s reputation as a leader in secure IoT-enabled smart home solutions
Overall, this case study demonstrates the importance of implementing end-to-end security in embedded devices and highlights the tangible benefits that can be achieved through a comprehensive and proactive security strategy.
Conclusion
In conclusion, the significance of end-to-end security in embedded devices cannot be overstated. As embedded systems become increasingly integrated into our daily lives, the potential impact of security breaches and cyberattacks on these devices grows exponentially. Implementing robust end-to-end security measures is crucial for safeguarding the privacy, safety, and trust of users and ensuring the continued success of organizations in the engineering industry.
The ongoing need for vigilance and innovation in embedded systems security is paramount. As technology continues to evolve, so do the threats and challenges faced by embedded devices. Organizations must remain agile and proactive in their approach to security, regularly updating their strategies and measures to stay ahead of emerging threats and vulnerabilities.
At RunTime Recruitment, we encourage organizations to prioritize security in their embedded devices. Our expertise in embedded systems and commitment to delivering results for both candidates and clients make us an ideal partner for organizations looking to stay ahead in the rapidly evolving world of embedded systems security. Together, we can create a safer, more secure future for embedded devices and the users who rely on them.
Hire Highly-Skilled Engineers with RunTime Recruitment
Our expert team of engineers-turned-recruiters offers in-depth knowledge of technical recruiting in the engineering industry.
If your company is looking to recruit highly-skilled engineers worldwide, contact us today and we will do the sourcing for you. Or if you’re an engineer looking for new opportunities, you can check RunTime Recruitment’s job site for job vacancies.