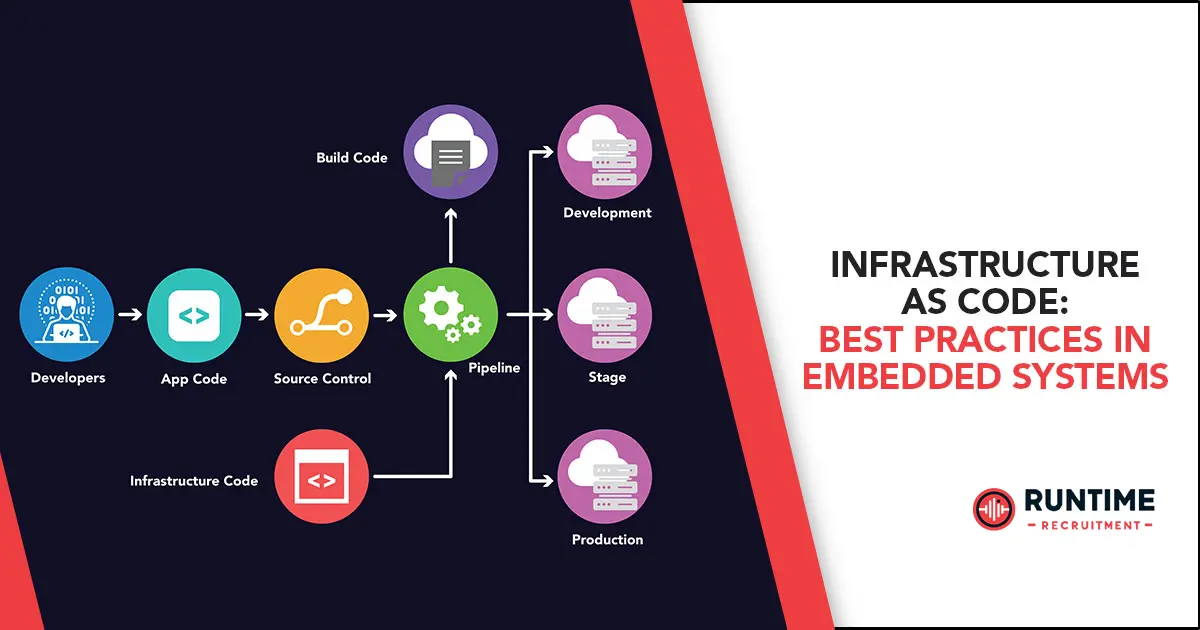
For decades, embedded systems engineers have relied on manual configuration to manage infrastructure, leading to time-consuming processes and inconsistencies. This article explores Infrastructure as Code (IaC), a revolutionary approach that treats infrastructure provisioning and management as code. Let’s discuss the significant benefits of IaC for embedded systems development, outlining best practices for implementation and showcasing practical examples to empower engineers to streamline their workflows.
Traditionally, embedded systems development involves manually configuring development environments, testing setups, and production deployments. This manual approach is error-prone, time-consuming, and hinders efficient collaboration. Infrastructure as Code (IaC) disrupts this paradigm by treating infrastructure as code, enabling its definition, provisioning, and management through automation. IaC tools leverage configuration files written in human-readable languages, eliminating the need for manual configuration and introducing numerous advantages for embedded systems development.
Benefits of IaC for Embedded Systems
IaC offers a compelling set of benefits that streamline embedded systems development:
- Reduced Time to Market: Manually configuring environments is a significant bottleneck. IaC automates provisioning, enabling rapid deployment of development, testing, and production environments. This translates to faster development cycles and quicker product delivery.
- Improved Consistency: IaC ensures identical infrastructure configurations across all environments (development, testing, production). This consistency minimizes bugs and errors that can arise from configuration discrepancies, leading to more reliable and predictable embedded systems.
- Enhanced Repeatability: When starting a new project or recovering from a disaster, recreating the infrastructure environment from scratch can be daunting. IaC eliminates this issue by enabling infrastructure recreation with a simple code execution, saving valuable time and effort.
- Increased Efficiency: Automating repetitive infrastructure management tasks with IaC frees engineers to focus on core development activities. This improves overall team productivity and allows engineers to dedicate their expertise to innovation.
- Improved Collaboration: IaC code can be stored in version control systems alongside application code, facilitating collaboration and knowledge sharing across teams. Team members can easily understand and modify infrastructure configurations, fostering better communication and streamlined development processes.
- Enhanced Security: IaC enforces security best practices consistently across deployments. Security policies can be embedded directly into the configuration code, ensuring that infrastructure adheres to security standards from the outset. This proactive approach significantly reduces security vulnerabilities.
Best Practices for IaC in Embedded Systems
To reap the full benefits of IaC in embedded systems development, consider these best practices:
- Choosing the Right Tool: Several popular IaC tools exist, each with its strengths and weaknesses. Popular choices include Terraform, a language-agnostic tool known for its flexibility, and Ansible, which leverages a powerful automation engine. Consider factors like project complexity, team familiarity, and desired level of control when selecting an IaC tool for your embedded systems development environment.
- Modular Design: Break down infrastructure configurations into reusable modules for better maintainability and scalability. This modular approach promotes code reuse and simplifies infrastructure management for large or complex projects.
- Version Control and Code Review: Integrate IaC code with existing version control systems (e.g., Git) to track changes, enable collaboration, and facilitate rollbacks if necessary. Additionally, implement code review processes to ensure IaC configurations adhere to security best practices and maintain code quality.
- Security Considerations: Security is paramount in IaC. Here are key considerations:
- Least Privilege: Implement the principle of least privilege within infrastructure configurations. Grant only the minimum permissions required for each component to function effectively.
- Secret Management: Sensitive information like passwords and access keys should never be stored directly in IaC code. Utilize secure secrets management tools to store and manage such credentials.
- Vulnerability Scanning: Regularly scan IaC code for potential vulnerabilities using purpose-built tools. This proactive approach helps identify and address security weaknesses before they can be exploited.
- Testing and Validation:
- Develop unit and integration tests for IaC code to ensure it delivers the desired infrastructure configurations. These tests can be automated and integrated into CI/CD pipelines for continuous validation.
- Integrate infrastructure testing into CI/CD pipelines. This ensures that any infrastructure changes introduced through IaC updates do not break downstream development or deployment processes.
- Monitoring and Observability:
- Implement monitoring tools to track resource utilization within the infrastructure provisioned by IaC. This enables proactive identification of potential bottlenecks or resource constraints.
- Establish logging and alerting mechanisms for infrastructure changes managed through IaC. This allows engineers to stay informed about infrastructure modifications and quickly address any arising issues.
Examples of IaC for Embedded Systems
IaC can be applied to various aspects of embedded systems development. Here are a few practical examples:
- Example 1: Provisioning a Development Environment: An IaC configuration can automate setting up a development environment with the necessary tools, libraries, and dependencies specific to the embedded system project. This could involve:
- Provisioning a virtual machine or container with the desired operating system.
- Installing essential development tools (compilers, debuggers, build tools).
- Downloading and configuring required libraries and frameworks.
- Setting environment variables specific to the project.
By automating this process, developers can quickly spin up identical development environments, reducing setup time and ensuring consistency across the team.
- Example 2: Configuring a Testing Framework: Testing embedded systems often requires specific hardware configurations and software tools. IaC can streamline this process by:
- Defining different testing environments with varying hardware configurations (e.g., memory, peripherals) simulated in software.
- Installing and configuring testing frameworks and tools specific to the embedded system under test.
- Setting up test data and test automation scripts within the testing environment.
This approach ensures consistent testing conditions across different test runs, leading to more reliable and repeatable test results.
- Example 3: Deploying an Embedded System to Production: Traditionally, deploying an embedded system to production hardware involved manual configuration and flashing of firmware. IaC can automate this process by:
- Provisioning the target production hardware (if applicable in a cloud environment).
- Configuring the target hardware with necessary settings (e.g., network settings, security policies).
- Transferring the compiled firmware image to the target hardware.
- Automating the flashing process to install the firmware onto the embedded device.
IaC streamlines production deployment, minimizing errors and ensuring consistent configuration across deployed systems.
Challenges and Considerations
While IaC offers significant benefits, there are challenges to consider:
- Vendor Lock-in: Some IaC tools can lead to vendor lock-in, where switching to a different tool becomes difficult due to proprietary configuration languages or integrations. Choosing a vendor-agnostic tool like Terraform can mitigate this risk.
- Security Risks: IaC configurations can introduce security vulnerabilities if not implemented securely. Following best practices like least privilege, secure secret management, and vulnerability scanning is crucial.
- Learning Curve: Adopting IaC requires engineers to learn new tools and concepts. However, the long-term benefits outweigh the initial learning investment. Numerous online resources, tutorials, and training programs are available to help engineers get started with IaC.
Wrapping Up
Infrastructure as Code (IaC) represents a paradigm shift in embedded systems development. By automating infrastructure provisioning and management, IaC unlocks a range of benefits, including faster time to market, improved consistency, enhanced repeatability, increased efficiency, and better collaboration. Implementing IaC with the best practices outlined in this article empowers embedded systems engineers to streamline workflows, improve development quality, and deliver more reliable products faster. As the industry continues to evolve, IaC is poised to play an increasingly vital role in the future of embedded systems development.
Hire the Best Engineers with RunTime
At RunTime, we are dedicated to helping you find the best Engineering talent for your recruitment needs. Our team consists of engineers-turned-recruiters with an extensive network and a focus on quality. By partnering with us, you will have access to great engineering talent that drives innovation and excellence in your projects.
Discover how RunTime has helped 423+ tech companies find highly qualified and talented engineers to enhance their team’s capabilities and achieve strategic goals.
On the other hand, if you’re a control systems engineer looking for new opportunities, RunTime Recruitment’s job site is the perfect place to find job vacancies.