With the increasing complexity and connectivity of industrial control systems (ICS), securing these systems has become more critical than ever. The potential risks and consequences of insecure ICS are staggering, ranging from operational disruptions and financial losses to reputational damage and even physical harm.
To ensure a safer Operational Technology environment, organizations need to implement effective security measures. In this article, let’s explore the best practices for securing industrial control systems.
Understanding the Threat Landscape
When it comes to securing industrial control systems (ICS) with a safer operational technology (OT) environment, it is crucial to have a deep understanding of the threat landscape. Industrial control systems are critical for the functioning of various industries, including medical, transport, industrial automation, audio/video, agriculture, energy, telecommunications, aerospace, and the Internet of Things (IoT). These systems control and monitor processes, ensuring that everything runs smoothly and efficiently.
However, with the increasing connectivity and interconnectivity of devices, the threat landscape has become more complex and sophisticated. Cybersecurity threats targeting ICS can have severe consequences, including financial losses, reputational damage, and even physical harm.
Common Threats to ICS
1. Unauthorized Access
One common threat to ICS is the possibility of unauthorized access. Malicious actors can exploit vulnerabilities in the system to gain access and manipulate or disrupt operations. This can be done through various means, such as:
- Exploiting weak passwords
- Using social engineering techniques to trick employees into divulging sensitive information
- Exploiting software vulnerabilities
2. Malware Attacks
Another significant threat is the risk of malware attacks. Malware can be introduced into the ICS through:
- Infected USB drives
- Phishing emails
- Compromised software updates
Once inside the system, malware can spread and cause significant damage, such as disrupting operations, stealing sensitive data, or even causing physical damage to equipment.
3. Targeted Attacks
Industrial Control Systems face the risk of targeted attacks specifically designed to exploit vulnerabilities in the system. These attacks can be highly sophisticated and may involve advanced techniques such as:
- Zero-day exploits
- Supply chain attacks
The motive behind such attacks can vary, ranging from financial gain to industrial espionage or even sabotage.
Best Practices for Securing Industrial Control Systems
To effectively secure industrial control systems, it is essential to implement a multi-layered approach that addresses these threats comprehensively. This approach includes:
1. Segmentation: Isolating Critical Systems
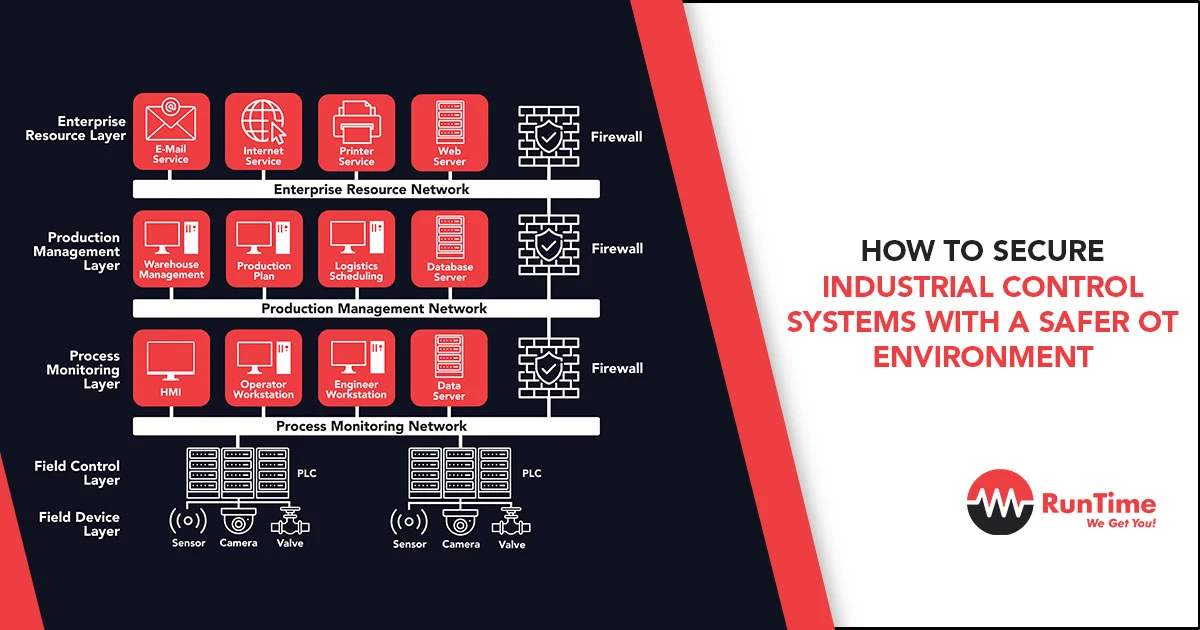
Network segmentation is a foundational security practice that involves dividing the network into smaller, manageable segments. This limits the spread of cyber threats and reduces the attack surface. For ICS, segmentation should isolate critical control systems from less sensitive networks, such as corporate IT environments. Employing demilitarized zones (DMZs) between IT and OT networks can further prevent unauthorized access.
2. Implement Robust Access Controls
Access to OT systems should be strictly controlled and monitored. Implement role-based access control (RBAC) to ensure that individuals have only the access necessary for their role. Multi-factor authentication (MFA) adds a layer of security, requiring users to provide two or more verification factors to gain access to the system.
By implementing strong access controls, organizations can limit access to critical systems and ensure that only authorized personnel can make changes. This includes practices such as:
- Using strong passwords
- Implementing two-factor authentication
- Regularly reviewing and updating user access privileges
3. Enhance Visibility and Monitoring
Visibility into OT networks is crucial for detecting anomalies and potential security incidents. Implementing security information and event management (SIEM) systems can aggregate logs from various sources, providing real-time monitoring and alerting for suspicious activities. Network monitoring tools specifically designed for OT environments can detect unusual network traffic patterns and signs of intrusion.
Enhancing visibility and monitoring is another crucial aspect of securing ICS. By implementing network monitoring tools and intrusion detection systems, organizations can detect and respond to suspicious activity promptly. This allows for early detection of potential threats and enables swift action to mitigate any potential damage.
4. Emphasizing Cybersecurity Awareness and Training
Human error remains one of the biggest vulnerabilities in cybersecurity. Regular training and awareness programs for employees can mitigate risks associated with phishing attacks and social engineering. Training should be tailored to the specific needs of OT personnel, emphasizing the criticality of physical safety and system reliability.
5. Regularly Update and Patch Systems
Vulnerabilities in software and firmware can be exploited by attackers to gain unauthorized access to ICS. Establish a comprehensive patch management program that includes regular updates and security patches for all components of the OT network. Since OT systems often require high availability, carefully plan and test updates to minimize disruptions.
Regularly updating and patching systems is essential to address known vulnerabilities. This includes:
- Regularly applying security updates and patches provided by vendors
- Conducting regular vulnerability assessments and penetration testing to identify and address any potential weaknesses
6. Implement Physical Security Measures
Physical security is an often overlooked aspect of securing ICS. Unauthorized physical access to OT devices can lead to tampering and cyber-physical attacks. Secure critical infrastructure with physical barriers, surveillance cameras, and access control systems to prevent unauthorized entry.
Physical security measures are also critical in protecting ICS. This includes implementing measures such as:
- Access control systems
- Surveillance cameras
- Physical barriers to prevent unauthorized access to critical infrastructure
7. Develop Robust Incident Response Plans
Despite best efforts, security incidents can still occur. A well-prepared incident response plan can minimize the impact of an attack. The plan should include procedures for isolating affected systems, eradicating threats, and restoring operations. Regularly conduct drills and exercises to ensure the readiness of the response team.
This includes:
- Defining clear roles and responsibilities
- Conducting regular training and drills
- Establishing communication channels to ensure a coordinated response
Final Word
In summary, it is crucial and challenging to secure Industrial Control Systems (ICS) in an Operational Technology (OT) environment. A comprehensive approach is necessary to address the diverse threat landscape. Neglecting ICS security poses significant risks, including operational, financial, and physical harm. Best practices such as network segmentation, robust access controls, improved visibility, cybersecurity awareness, and regular system updates are fundamental for effective ICS security. Additionally, prioritizing physical security and having a well-prepared incident response plan is vital for comprehensive protection. Organizations must adopt these measures to safeguard their critical infrastructure against cyber threats, ensuring operational resilience and safety in the digital age.
Hire Control Systems Engineers with RunTime
At RunTime, we are dedicated to helping you find the best Control Systems Engineering talent for your recruitment needs. Our team consists of engineers-turned-recruiters who have an extensive network and a focus on quality. By partnering with us, you will have access to great engineering talent that drives innovation and excellence in your projects.
Discover how RunTime has helped 423+ tech companies find highly qualified and talented engineers to enhance their team’s capabilities and achieve strategic goals.
On the other hand, if you’re a control systems engineer looking for new opportunities, RunTime Recruitment’s job site is the perfect place to find job vacancies.