In the rapidly evolving landscape of technology, the imperative of safeguarding valuable intellectual property and ensuring the integrity of custom hardware solutions has never been more pressing. As businesses navigate the digital realm, the demand for robust security measures within Field-Programmable Gate Array (FPGA) systems has surged. FPGA technology offers unparalleled flexibility and performance, making it a preferred choice for implementing specialized hardware solutions.
However, this very adaptability also introduces vulnerabilities that can be exploited by malicious entities for IP theft or system compromise. This exploration delves into the significance of fortifying FPGA systems, addressing the risks associated with IP theft and tampering, and delving into effective strategies to fortify data security and maintain the reliability of these systems. By comprehending potential threats and implementing proactive security protocols, organizations can minimize risks and bolster the dependability of their FPGA-driven innovations.
Understanding IP Theft and Tampering Risks
Implications of IP Theft in FPGA Designs
The theft of Intellectual Property (IP) poses significant risks to both the original IP creators and the end-users. IP theft refers to the unauthorized acquisition, use, or distribution of proprietary designs, algorithms, or any other form of intellectual property. When it comes to FPGA designs, the implications of IP theft can be severe.
Impact on Original Creators
- Loss of Competitive Advantage: Companies invest significant resources in developing innovative IP cores to differentiate their products in the market. When this IP is stolen, the competitive advantage is compromised, leading to financial losses and reputational damage.
- Revenue Loss: Licensing IP cores is a common practice in the FPGA industry. When stolen, companies lose out on potential revenue streams, impacting their bottom line.
- Legal Consequences: IP theft is a violation of intellectual property rights and can result in legal battles, further draining resources and time.
Impact on End-Users
- Security Risks: Tampered IP cores can contain malicious code or backdoors that compromise the security of FPGA-based systems. This can lead to data breaches, system failures, or unauthorized access.
- Reliability Concerns: Tampered IP cores may introduce errors or vulnerabilities in the design, affecting the reliability and performance of the FPGA system.
Types of Tampering Threats Faced by FPGA Systems
FPGA systems are vulnerable to various tampering threats that can jeopardize the integrity and security of the designs. Understanding these threats is crucial for implementing robust security measures.
Hardware Attacks
- Silicon-Level Attacks: Attackers can tamper with the physical structure of the FPGA chip through techniques like reverse engineering, microprobing, or laser fault injection.
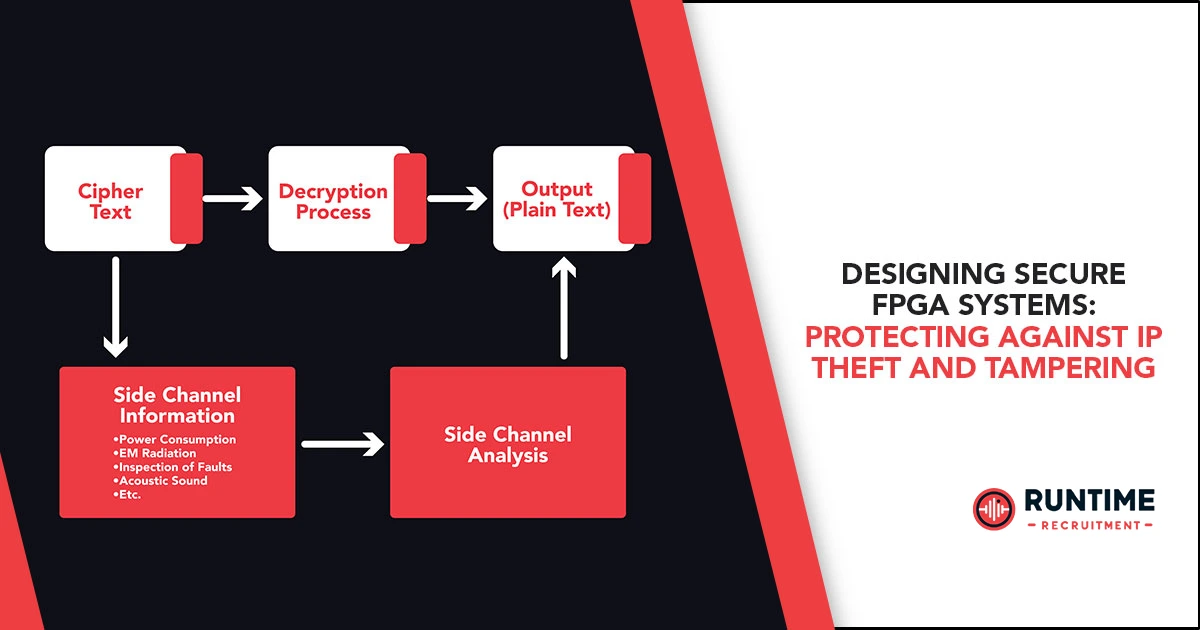
- Side-Channel Attacks: By analyzing the power consumption, electromagnetic emissions, or timing characteristics of the FPGA, attackers can extract sensitive information or manipulate the system.
Design-Level Attacks
- IP Infringement: Unauthorized access to, modification, or replication of IP cores can result in IP theft and compromise the functionality of the FPGA design.
- Trojan Insertion: Malicious modifications to the design, such as inserting Trojans or hidden functionalities, can create security vulnerabilities or backdoors.
Configuration Attacks
- Bitstream Manipulation: Altering the configuration bitstream of the FPGA can lead to unauthorized changes in the design or behavior of the system.
- Remote Configuration: In cases where FPGAs are remotely configured, the transmission of configuration data over insecure channels can be intercepted or modified.
By understanding the risks associated with IP theft and tampering in FPGA designs, stakeholders can take proactive steps to safeguard their intellectual property and ensure the security of their systems.
Common Vulnerabilities in FPGA Systems
Identifying Weak Points in FPGA Systems.
FPGAs (Field-Programmable Gate Arrays) are crucial components in various industries due to their adaptability and reconfigurability. However, this adaptability also brings about vulnerabilities that can be exploited by malicious actors. Understanding and addressing these vulnerabilities are essential to enhancing the security of FPGA systems.
Types of Vulnerabilities in FPGA Systems
- Configuration Vulnerabilities: Unauthorized access to configuration data can lead to system reconfiguration by unauthorized entities, opening the door to potential exploits and compromises.
- Side-Channel Attacks: FPGAs are vulnerable to side-channel attacks, where attackers monitor power consumption or electromagnetic emissions to extract sensitive information, posing a significant threat to data confidentiality.
- Design Flaws: Errors in the FPGA design process can introduce unintended vulnerabilities that adversaries can exploit, emphasizing the need for rigorous design validation and testing.
- Hardware Trojans: Malicious modifications to FPGA hardware, known as hardware Trojans, can compromise system integrity and functionality, underscoring the importance of supply chain security.
Impact of Security Breaches on FPGA Functionality
Security breaches in FPGA systems can have far-reaching consequences, including data breaches, system malfunctions, or complete operational shutdowns. These incidents not only result in data loss but also jeopardize the reliability and confidentiality of critical systems reliant on FPGAs.
Mitigating Vulnerabilities in FPGA Systems
- Secure Boot Process: Implementing a secure boot process can prevent unauthorized firmware modifications and ensure the integrity of the FPGA configuration.
- Runtime Monitoring: Continuous monitoring of FPGA operation can help detect abnormal behavior indicative of security breaches, enabling prompt response and mitigation.
- Vulnerability Patching: Regularly applying security patches and updates to FPGA firmware and software can address known vulnerabilities and strengthen system defenses.
- Security Training: Providing security awareness training to FPGA system users and administrators can help prevent common security pitfalls and enhance overall system security.
Security Measures and Solutions
Encryption Techniques for Protecting FPGA IP
One of the fundamental aspects of securing FPGA designs is the use of encryption techniques. Encryption helps in protecting the confidentiality and integrity of the IP stored within the FPGA. By encrypting the bitstream or configuration files, organizations can prevent unauthorized access and tampering of their designs. Common encryption methods include symmetric and asymmetric encryption, as well as hashing algorithms.
Implementing Secure Coding Practices
Another vital aspect of FPGA security is the implementation of secure coding practices during the design phase. By following secure coding guidelines and best practices, developers can reduce the risk of vulnerabilities and exploits in FPGA designs. This includes proper input validation, secure memory management, and adherence to coding standards. Additionally, conducting security audits and code reviews can help identify and mitigate potential security flaws.
Role of Secure Boot Processes in FPGA Security
Secure boot processes play a crucial role in ensuring the integrity of FPGA systems during the boot-up sequence. By verifying the authenticity and integrity of the initial boot code and subsequent stages, secure boot mechanisms help prevent unauthorized firmware modifications and attacks. Implementing secure boot processes, such as digital signatures and secure bootloaders, can significantly enhance the overall security posture of FPGA devices.
In addition to encryption, secure coding, and secure boot processes, organizations can further enhance FPGA security by integrating hardware security modules (HSMs) for key management and cryptographic operations. HSMs provide a secure environment for storing and handling encryption keys, ensuring that sensitive data remains protected from unauthorized access.
Furthermore, continuous monitoring and threat intelligence sharing are essential components of a comprehensive FPGA security strategy. By actively monitoring FPGA systems for anomalous behavior and sharing threat intelligence with industry peers, organizations can stay ahead of emerging threats and vulnerabilities.
Incorporating robust security measures and solutions is essential for protecting FPGA systems against potential threats and vulnerabilities. By leveraging encryption techniques, secure coding practices, secure boot processes, and HSMs, organizations can fortify the security of their FPGA designs and uphold the integrity of their intellectual property and sensitive data.
Hardware and Software Security Integration
Utilizing Both Hardware and Software Defenses for Comprehensive Security
Securing data and information is crucial for individuals and organizations. The integration of hardware and software security measures has emerged as a powerful strategy to fortify defenses against evolving cyber threats.
Hardware Security
- Physical Protection: Hardware security employs physical safeguards like biometric authentication, secure enclaves, and hardware tokens to shield sensitive data from unauthorized access. These measures ensure that the underlying hardware remains a formidable barrier even if software defenses are breached.
- Tamper Resistance: Designing hardware components to be tamper-resistant adds an extra layer of protection. Tamper resistance enhances the overall security posture by making it challenging for attackers to manipulate or extract data from devices.
Software Security
- Encryption: Implementing robust encryption techniques safeguards data at rest and in transit. Encryption renders data unreadable to unauthorized parties, even if they manage to access it, thereby maintaining confidentiality.
- Access Controls: Stringent access controls, multi-factor authentication, and timely software updates are fundamental pillars of software security. These measures ensure that only authorized individuals can access critical systems and information.
Benefits of Multi-Layered Security Approaches
- Resilience: Multi-layered security combines the strengths of hardware and software defenses, creating a resilient security ecosystem capable of withstanding diverse cyber threats. This resilience is crucial in safeguarding against sophisticated attacks.
- Defense in Depth: The principle of defense in depth is exemplified through multi-layered security. Even if one layer is compromised, other layers act as barriers, impeding attackers’ progress and limiting the impact of breaches.
- Regulatory Compliance: Adhering to industry regulations is a top priority for organizations. A multi-layered security approach helps meet compliance standards effectively, ensuring that data handling practices align with legal requirements.
- Continuous Monitoring: Implementing continuous monitoring mechanisms allows real-time threat detection and response. Organizations can swiftly identify and mitigate security incidents by actively monitoring hardware and software systems.
- Adaptability to Emerging Threats: Combining hardware and software security enables organizations to adapt to new and emerging threats. This adaptability is crucial in an ever-changing threat landscape, where proactive defense strategies are essential.
Integrating hardware and software security measures offers a robust defense strategy that enhances data protection, mitigates risks, and upholds the confidentiality and integrity of sensitive information. By embracing a multi-layered security approach, organizations can fortify their defenses and stay resilient against evolving cybersecurity challenges.
Regulatory Compliance and Standards
In the realm of Field-Programmable Gate Arrays (FPGAs), ensuring regulatory compliance and meeting established security standards are paramount. Let’s delve into the essential aspects of adhering to industry regulations and standards in FPGA security.
Overview of Industry Regulations for FPGA Security
Understanding the regulatory landscape is crucial for FPGA security. Various regulatory bodies, such as NIST (National Institute of Standards and Technology) and ISO (International Organization for Standardization), set guidelines to safeguard FPGA applications from potential security risks. Compliance with these regulations not only ensures data protection but also fosters trust among stakeholders.
Adhering to Established Security Standards
To fortify FPGA security, organizations must adhere to established security standards. Standards like FIPS (Federal Information Processing Standards) and Common Criteria provide a framework for implementing robust security measures in FPGA designs. By aligning with these standards, companies can mitigate vulnerabilities and enhance the overall security posture of their FPGA solutions.
Importance of Continuous Compliance Monitoring
In the dynamic landscape of technology and security threats, continuous compliance monitoring is essential for FPGA security. Regular audits, vulnerability assessments, and proactive security measures help in identifying and addressing potential risks promptly. By incorporating a culture of continuous compliance monitoring, organizations can stay ahead of emerging threats and ensure the resilience of their FPGA systems.
Role of Encryption and Access Control
Encryption plays a vital role in safeguarding sensitive data processed through FPGAs. Implementing strong encryption algorithms and robust access control mechanisms are fundamental in protecting data integrity and confidentiality. By integrating encryption and access control measures into FPGA designs, organizations can enhance data security and thwart unauthorized access attempts.
Impact of Non-Compliance on Business Operations
Non-compliance with industry regulations and security standards can have severe repercussions on business operations. Apart from legal consequences, data breaches and security incidents resulting from non-compliance can damage a company’s reputation and financial stability. It is crucial for organizations to understand the risks associated with non-compliance and prioritize regulatory adherence to safeguard their interests.
Future Trends in FPGA Security
The field of FPGA security is continuously evolving, with new trends and technologies shaping the landscape. Emerging trends such as hardware-based security features, machine learning for threat detection, and quantum-resistant algorithms are expected to revolutionize FPGA security practices. Staying abreast of these trends and incorporating innovative security measures is vital for organizations looking to stay ahead of cyber threats and ensure the long-term security of their FPGA deployments.
By prioritizing regulatory compliance, adhering to stringent security standards, emphasizing continuous compliance monitoring, implementing encryption and access control measures, understanding the impact of non-compliance on business operations, and staying informed about future trends, businesses can strengthen the security posture of their FPGA solutions. Proactive security measures not only mitigate risks but also instill confidence in the reliability and integrity of FPGA deployments, fostering a secure and compliant operational environment.
Case Studies and Lessons Learned
Analyzing Past Incidents of IP Theft and Tampering
In this section, we delve into real-world case studies of intellectual property theft and tampering. By examining these incidents, we can uncover valuable insights and lessons that can be applied to enhance security practices.
Extracting Key Insights for Better Security Practices
Through the analysis of past cases, we aim to extract key insights that can help organizations strengthen their security measures. By learning from these incidents, companies can proactively safeguard their intellectual property and prevent future breaches.
- Case studies provide a unique opportunity to understand the strategies and vulnerabilities that led to IP theft and tampering. By reviewing these cases, we can identify common patterns and trends that highlight the importance of robust security protocols.
- Lessons learned from past incidents emphasize the significance of employee training and awareness programs. Human error and negligence often serve as entry points for cybercriminals. By educating staff on cybersecurity best practices and implementing access controls, organizations can reduce the likelihood of internal threats.
- Moreover, collaboration with industry experts and regulatory bodies can offer valuable insights into emerging threats and compliance requirements. By staying informed about the latest security trends and regulations, companies can adapt their strategies to protect sensitive information effectively.
Analyzing case studies and lessons learned from past incidents of IP theft and tampering is crucial for developing robust security frameworks. By leveraging these insights, organizations can fortify their defenses, mitigate risks, and safeguard their intellectual property in an increasingly digital landscape.
Enhancing Security Measures through Technology Integration
Integrating advanced security technologies is paramount in safeguarding intellectual property. Utilizing encryption tools, access controls, and multi-factor authentication can significantly enhance data protection. Additionally, implementing intrusion detection systems and security analytics can help identify and respond to potential threats proactively.
Continuous Monitoring and Incident Response
Establishing a comprehensive monitoring system is essential for detecting unauthorized access and unusual activities. By continuously monitoring network traffic and system logs, organizations can swiftly identify security breaches and initiate timely incident response procedures. This proactive approach minimizes the impact of security incidents and aids in preserving the integrity of intellectual property.
Training and Awareness Programs
Empowering employees with cybersecurity awareness is a fundamental aspect of strengthening an organization’s security posture. Conducting regular training sessions on phishing awareness, social engineering tactics, and data handling best practices can mitigate the risks posed by human error. Encouraging a culture of security consciousness among staff members fosters a collective responsibility towards protecting sensitive information.
Building Resilience through Regular Security Assessments
Conducting periodic security assessments and penetration testing exercises is essential for evaluating the effectiveness of security controls and identifying vulnerabilities. By conducting thorough assessments, organizations can proactively address weaknesses in their security infrastructure and implement necessary remediation measures. This proactive approach enhances the resilience of the organization against potential cyber threats.
Collaboration and Information Sharing
Engaging in collaborative efforts with industry peers, cybersecurity experts, and law enforcement agencies can provide valuable insights into emerging threats and best practices. Sharing information on security incidents, threat intelligence, and effective security strategies can collectively strengthen the cybersecurity posture of the industry. Additionally, participating in information sharing platforms and threat intelligence exchanges facilitates the timely dissemination of critical security alerts and proactive defense measures.
Adhering to Compliance Standards and Regulations
Compliance with industry regulations and data protection laws is essential for ensuring the legal and ethical handling of intellectual property. Organizations must stay abreast of regulatory requirements, such as GDPR, HIPAA, or PCI DSS, and implement appropriate controls to safeguard sensitive information. Compliance frameworks serve as guidelines for establishing robust security practices and maintaining the trust of customers and stakeholders.
Incorporating Risk Management Strategies
Developing a comprehensive risk management framework is vital for identifying, assessing, and mitigating potential security risks. By conducting risk assessments, organizations can prioritize security investments, allocate resources effectively, and implement tailored risk mitigation strategies. Adopting a risk-based approach to security enables organizations to proactively address vulnerabilities and protect intellectual property from evolving threats.
Conclusion
Designing secure FPGA systems is crucial in safeguarding against IP theft and tampering. By implementing robust security measures such as encryption, authentication, and monitoring, developers can mitigate the risks associated with unauthorized access and modifications to their intellectual property. It is imperative for companies and individuals alike to prioritize security in FPGA system design to ensure the integrity and confidentiality of their sensitive information.
The evolving landscape of intellectual property theft and tampering necessitates a proactive and multi-layered approach to cybersecurity. By analyzing past case studies, extracting valuable insights, and implementing advanced security measures, organizations can fortify their defenses and safeguard their intellectual assets effectively. Embracing technology integration, continuous monitoring, employee training, security assessments, collaboration, compliance adherence, and risk management are integral components of a robust security framework. By prioritizing cybersecurity and fostering a culture of vigilance, organizations can mitigate risks, protect intellectual property, and uphold the trust of their stakeholders in an increasingly interconnected digital environment.