In the realm of embedded systems, the bootloader is often an unsung hero. While it operates silently in the background, its functionality is critical for system initialization, firmware updates, and even device security. Designing a robust bootloader can be both challenging and rewarding, as it lays the foundation for reliable embedded system operation.
This article explores the essential aspects of bootloader development, including its role in embedded systems, the best practices to follow, and the common pitfalls to avoid. Whether you’re designing a bootloader from scratch or enhancing an existing one, this guide will provide the insights you need to succeed.
What Is a Bootloader and Why Is It Important?
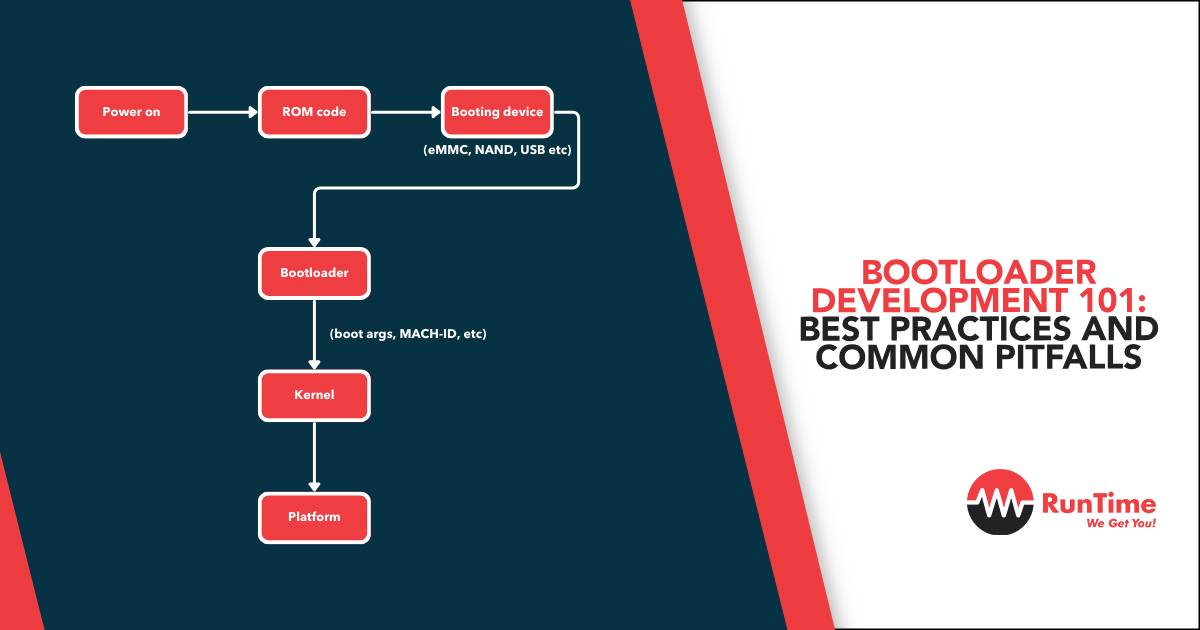
A bootloader is a small piece of code that runs immediately after a system powers up or resets. Its primary role is to initialize the hardware, load the main application firmware into memory, and transfer control to it. In some systems, the bootloader also handles critical functions like firmware updates and system recovery.
Key Responsibilities of a Bootloader:
- Hardware Initialization:
- Sets up clocks, memory, and basic peripherals to prepare the system for the application.
- Firmware Loading:
- Locates, verifies, and loads the main application code into executable memory.
- Firmware Updates:
- Facilitates over-the-air (OTA) or wired updates of the application firmware.
- Security:
- Validates firmware integrity using cryptographic methods to prevent unauthorized or corrupted code execution.
- Diagnostics:
- Provides a fallback mechanism for debugging or recovering from errors.
Why You Need a Bootloader:
- Scalability: Enables easy firmware updates without requiring physical access to the device.
- Recovery Mechanism: Allows recovery from firmware corruption or failed updates.
- Security: Ensures only authenticated and verified firmware is executed.
- System Flexibility: Supports multiple application firmware versions or configurations.
Bootloader Types
Depending on the use case, bootloaders can vary in complexity. Here are the common types of bootloaders:
1. Primary Bootloader
The primary bootloader is embedded in ROM or protected flash and is responsible for low-level system initialization. It’s often minimalistic and serves as a first-stage loader.
2. Secondary Bootloader
This is a more feature-rich bootloader that resides in flash memory. It handles firmware updates, security validation, and application loading.
3. OTA Bootloader
Designed for IoT and wireless applications, this bootloader supports over-the-air updates. It incorporates network stacks to download and verify firmware updates securely.
Bootloader Development: Best Practices
Developing a robust and reliable bootloader involves careful planning and implementation. Below are some best practices to follow:
1. Plan for Scalability
Your bootloader should be flexible enough to accommodate future requirements, such as additional security features or OTA updates.
Tips:
- Design modular code with separate functions for hardware initialization, firmware verification, and application loading.
- Use configuration files or constants to allow parameter adjustments without modifying the core code.
2. Minimize Bootloader Size
Bootloaders typically run from limited memory, so keeping the code compact is essential.
Tips:
- Avoid including unnecessary features or libraries.
- Use low-level drivers instead of full hardware abstraction layers (HALs).
- Optimize code for memory usage and performance.
3. Implement Robust Firmware Update Mechanisms
Firmware updates are one of the key features of modern bootloaders. Ensure updates are reliable and error-resistant.
Best Practices:
- Use dual-bank flash or firmware slots to allow updates without erasing the running firmware.
- Add rollback mechanisms to restore the previous firmware version if the update fails.
- Validate firmware integrity (e.g., using CRC, hash, or digital signatures) before applying updates.
4. Prioritize Security
Bootloaders are a potential attack vector for malicious actors. Implement security features to protect your system.
Best Practices:
- Encrypt firmware images to prevent unauthorized access.
- Use digital signatures to verify firmware authenticity.
- Store sensitive keys in secure memory or hardware security modules (HSMs).
5. Optimize Boot Time
A slow boot process can frustrate users and waste power in time-critical applications. Strive to minimize boot time.
Tips:
- Perform only essential hardware initialization in the bootloader; leave application-specific configurations to the main firmware.
- Use efficient algorithms for firmware verification.
- Load firmware directly into memory without unnecessary copying.
6. Use Debug-Friendly Features
Debugging bootloader issues can be challenging due to limited resources and early-stage execution. Make debugging easier by incorporating diagnostic features.
Best Practices:
- Add a simple UART or LED-based interface for debugging and status reporting.
- Use bootloader logs to store critical information about boot failures.
- Include a safe boot mode for recovery or troubleshooting.
7. Implement Watchdog Management
Ensure the system watchdog timer is properly managed during the boot process to avoid unexpected resets.
Tips:
- Refresh the watchdog timer periodically during the boot process.
- Disable the watchdog temporarily if necessary during critical operations like firmware updates.
8. Separate Application and Bootloader
Keep the application and bootloader code independent to simplify development and maintenance.
Best Practices:
- Define a clear memory map with distinct regions for the bootloader and application.
- Use vector table relocation to allow the application to manage interrupts independently.
9. Document and Test Thoroughly
Comprehensive documentation and rigorous testing are critical for a reliable bootloader.
Best Practices:
- Document the memory map, update process, and security features.
- Test edge cases, such as power loss during firmware updates or corrupted firmware.
- Use hardware-in-the-loop (HIL) testing to validate the bootloader in real-world conditions.
Common Pitfalls and How to Avoid Them
Even experienced engineers can encounter challenges when developing bootloaders. Here are some common pitfalls and how to avoid them:
1. Overcomplicating the Bootloader
Including too many features in the bootloader can increase its size and complexity, making it harder to debug and maintain.
Solution:
- Focus on essential functions like firmware loading and validation. Offload advanced features to the application.
2. Ignoring Security
Many developers overlook security, leaving the system vulnerable to attacks like firmware tampering or unauthorized updates.
Solution:
- Always include firmware integrity checks and authentication mechanisms.
- Encrypt sensitive data and use secure key storage.
3. Poor Memory Management
Incorrect memory allocation can lead to conflicts between the bootloader and application.
Solution:
- Define a clear and fixed memory map at the start of the project.
- Use linker scripts to enforce memory boundaries.
4. Failing to Plan for Failure
Firmware updates can fail due to power loss or corrupted data, leaving the system in an unusable state.
Solution:
- Use dual-bank or fallback mechanisms to ensure the system can recover from update failures.
5. Neglecting Hardware Variability
Bootloaders often need to run on different hardware configurations. Hardcoding parameters can lead to compatibility issues.
Solution:
- Use configuration files or compile-time macros to adapt to different hardware variants.
6. Skipping Testing
Insufficient testing can result in hard-to-diagnose issues that only appear in production.
Solution:
- Test the bootloader under various conditions, including low power, high temperatures, and simulated hardware failures.
Real-World Bootloader Use Cases
1. IoT Device with OTA Updates
An IoT device uses an OTA bootloader to update firmware securely over Wi-Fi. The bootloader:
- Validates updates using cryptographic signatures.
- Supports rollback to a previous version if the update fails.
- Encrypts firmware images to protect intellectual property.
2. Automotive ECU Bootloader
An automotive Electronic Control Unit (ECU) bootloader enables secure firmware updates during vehicle maintenance. The bootloader:
- Uses dual-bank flash for update safety.
- Implements secure boot to prevent unauthorized firmware.
- Logs update events for traceability.
3. Industrial Controller with Recovery Mode
An industrial controller bootloader includes a recovery mode for field technicians. The bootloader:
- Provides a UART interface for manual firmware upload.
- Detects and recovers from corrupted firmware.
- Displays status messages via an LED indicator.
Conclusion
Bootloader development is a critical aspect of embedded system design, enabling features like secure updates, system recovery, and application management. While the task can be challenging, following best practices—such as prioritizing security, optimizing boot time, and testing thoroughly—can lead to a robust and reliable bootloader.
By avoiding common pitfalls like overcomplicating the bootloader or neglecting failure scenarios, you can ensure your system is resilient and scalable. Whether you’re working on IoT devices, automotive systems, or industrial controllers, a well-designed bootloader will serve as the backbone of your embedded system’s reliability and flexibility.
Bootloaders may operate behind the scenes, but their impact on system performance and reliability is anything but hidden. Invest the time to design and implement a robust bootloader, and you’ll set your embedded system up for success.