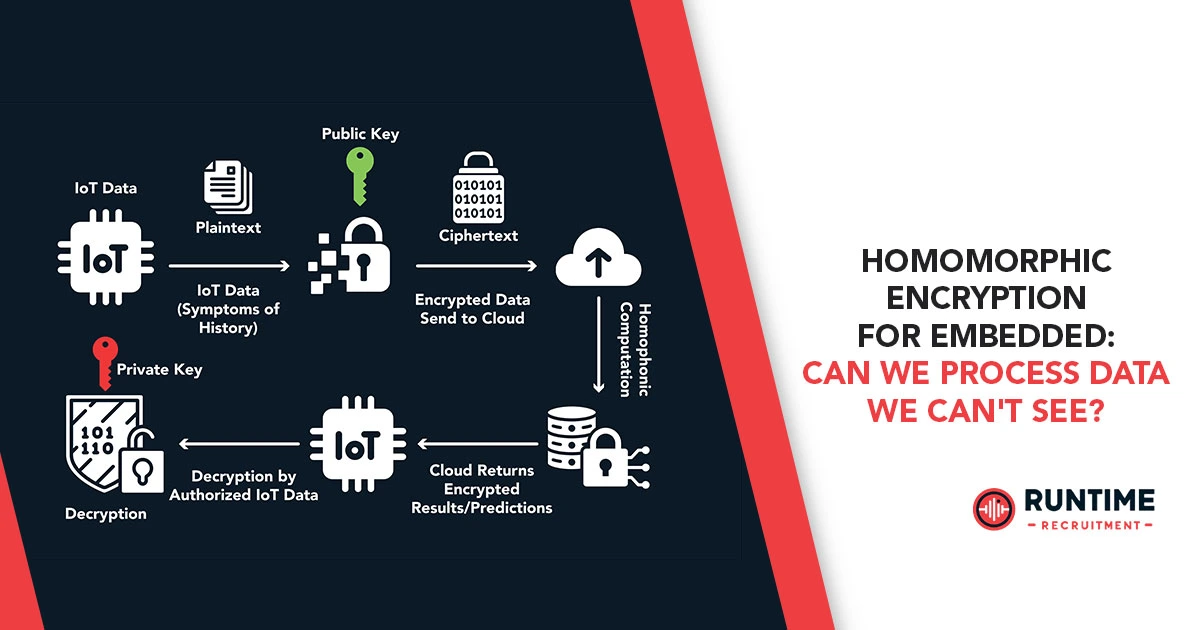
In an era where data privacy and security are paramount, embedded systems face increasing pressure to handle sensitive information securely. Traditional encryption methods protect data at rest and in transit but require decryption before processing—exposing it to potential vulnerabilities.
Homomorphic Encryption (HE) offers a groundbreaking alternative: the ability to compute on encrypted data without ever decrypting it.
For embedded engineers, this raises critical questions:
- Is HE practical for resource-constrained devices?
- What are the real-world trade-offs between security and performance?
- Can we process data we can’t even see?
This article explores the feasibility of homomorphic encryption in embedded systems, its challenges, and emerging solutions that could revolutionize secure edge computing.
1. What is Homomorphic Encryption?
Homomorphic encryption is a cryptographic technique that allows computations to be performed on encrypted data, producing an encrypted result that, when decrypted, matches the result of operations performed on the plaintext.
Types of Homomorphic Encryption
- Partially Homomorphic Encryption (PHE): Supports only one type of operation (either addition or multiplication).
- Example: RSA (multiplicative), Paillier (additive).
- Somewhat Homomorphic Encryption (SHE): Supports limited operations before noise overwhelms the ciphertext.
- Fully Homomorphic Encryption (FHE): Supports arbitrary computations on encrypted data (both addition and multiplication).
FHE is the “holy grail” but comes with significant computational overhead, making it challenging for embedded systems.
2. Why Homomorphic Encryption in Embedded Systems?
Embedded devices—ranging from IoT sensors to medical implants—often handle sensitive data. HE could enable:
A. Privacy-Preserving Edge Computing
- Process data locally without exposing raw information.
- Useful in healthcare (patient monitoring), industrial IoT (proprietary sensor data), and smart homes.
B. Secure Outsourced Computation
- Offload processing to untrusted edge/cloud servers while keeping data encrypted.
C. Regulatory Compliance
- Meet GDPR, HIPAA, and other privacy laws by minimizing data exposure.
3. Challenges of Homomorphic Encryption in Embedded Systems
Despite its promise, HE faces major hurdles in embedded applications:
A. High Computational Overhead
- FHE operations are orders of magnitude slower than plaintext computations.
- Polynomial multiplications, bootstrapping (noise reduction), and large ciphertext sizes strain limited CPU resources.
B. Memory Constraints
- HE ciphertexts can be 100x–1000x larger than plaintext data.
- A single 32-bit integer encrypted with FHE may require kilobytes of storage.
C. Power Consumption
- Prolonged HE computations drain battery-powered devices quickly.
D. Limited Practical Implementations
- Most HE schemes (e.g., BGV, CKKS, TFHE) are optimized for servers, not microcontrollers.
4. Current Approaches to Making HE Work in Embedded
Researchers and engineers are exploring optimizations to bring HE into the embedded world:
A. Lightweight HE Schemes
- CKKS for Approximate Arithmetic: Allows trading precision for performance (useful in ML inference).
- BGV/BFV for Integer Operations: More efficient for exact computations.
B. Hardware Acceleration
- FPGA/ASIC Accelerators: Dedicated HE coprocessors (e.g., Intel HEXL, Microsoft SEAL).
- Approximate Computing: Reducing bit-width for faster operations.
C. Hybrid Encryption Models
- Combine HE with secure multi-party computation (SMPC) or functional encryption to offload only critical operations.
D. Optimized Libraries for Embedded
- Microsoft SEAL, PALISADE, HElib (with ARM Cortex optimizations).
- TinyHE: Experimental HE libraries for microcontrollers.
5. Real-World Use Cases & Feasibility
| Application | HE Feasibility | Why? |
| Medical Implants | 🟡 Moderate | Low-latency HE possible with PHE/SHE. |
| Industrial IoT | 🟢 High (for some) | Batch processing can tolerate HE latency. |
| Autonomous Vehicles | 🔴 Low (today) | Real-time FHE too slow for safety-critical systems. |
| Smart Home Hubs | 🟡 Moderate | Can use HE for selective privacy-sensitive tasks. |
Case Study: Private Sensor Data Aggregation
A smart city collects encrypted traffic data from edge devices. Using additive HE (Paillier), the server aggregates speeds without decrypting individual inputs—preserving privacy while computing averages.
6. The Future: Can Embedded Systems Process Data They Can’t See?
A. Near-Term (Next 5 Years)
- SHE/PHE adoption in select embedded applications.
- Hardware-accelerated HE (RISC-V extensions, FPGA overlays).
B. Long-Term (10+ Years)
- FHE at the edge with quantum-resistant schemes.
- Neuromorphic computing for energy-efficient encrypted processing.
Conclusion: Is HE Ready for Embedded?
Homomorphic encryption is not yet practical for most real-time embedded systems, but progress is accelerating.
For now:
- Use HE selectively (e.g., non-real-time data aggregation).
- Leverage hybrid models (combine HE with TEEs like ARM TrustZone).
- Watch for hardware advancements (dedicated HE accelerators).
The dream of processing data we can’t see is within reach—but embedded engineers must balance security, performance, and power constraints wisely.