Designing robust bootloaders is a critical aspect of ensuring reliable firmware updates for embedded systems. A bootloader is the initial software program that runs when a system is powered on, responsible for loading the operating system. In the context of firmware updates, a well-designed bootloader is essential for seamlessly updating the system’s software without the risk of bricking the device. This process is crucial for fixing bugs, enhancing security, and adding new features.
Robust bootloaders not only facilitate the update process but also provide mechanisms for error detection, recovery, and rollback in case of update failures. By focusing on designing secure, efficient, and error-tolerant bootloaders, developers can significantly enhance the overall reliability and longevity of embedded systems. This introduction will delve into key principles and strategies for designing robust bootloaders to ensure smooth and reliable firmware updates in embedded systems.
Understanding Bootloader Fundamentals
Bootloader Functions and Responsibilities
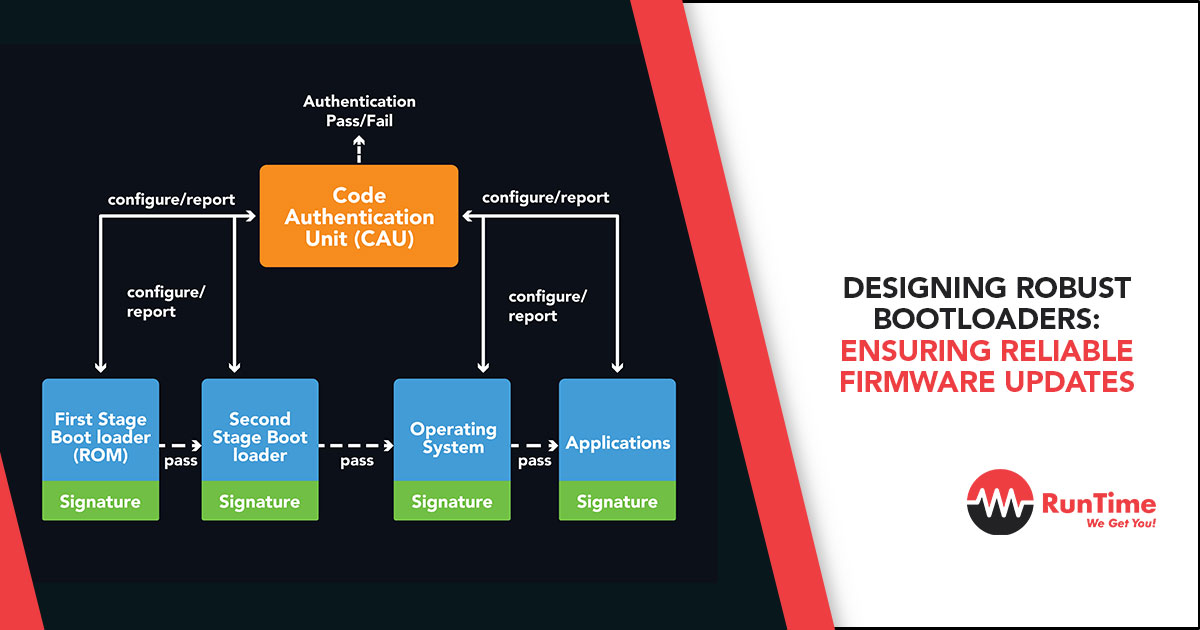
The bootloader plays a crucial role in the startup process of a device. It is responsible for initializing the hardware, setting up the environment, and loading the operating system or firmware into the memory. The bootloader ensures a smooth transition from the hardware initialization phase to the execution of the main firmware, making it a critical component in the boot process.
Bootloader vs. Firmware: Clarifying the Difference
One common point of confusion is differentiating between the bootloader and firmware. While both are essential components of embedded systems, they serve distinct purposes. The bootloader is a specialized program that initializes the system hardware and facilitates the loading of the main firmware or operating system. In contrast, firmware refers to the software that provides specific functionalities to the device, directly interacting with the hardware components. Understanding this distinction is vital for developers to design efficient and reliable embedded systems.
Bootloader Execution Process
To comprehend the bootloader fully, it is essential to delve into its execution process. Typically located in a dedicated memory area, the bootloader is the first code that executes upon device power-up or reset. The execution process involves several critical steps, including memory initialization, hardware configuration, and transitioning control to the main firmware or operating system. Developers must optimize each step to minimize boot time and enhance overall system performance.
Importance of Bootloader Security
Ensuring the security of embedded systems is paramount. The bootloader, being the initial code that runs on the device, plays a crucial role in system security. Implementing secure bootloader practices, such as code signing, secure boot, and encryption, helps prevent unauthorized access, tampering, or malware injection. This section explores the significance of bootloader security measures and best practices to safeguard embedded systems from potential threats.
Bootloader Customization and Development Tools
Customizing the bootloader to meet specific project requirements is common in embedded systems development. Various development tools, such as integrated development environments (IDEs), debuggers, and flash programmers, facilitate bootloader customization and testing. Understanding how to leverage these tools effectively can streamline the bootloader development process, accelerate project timelines, and ensure the robustness of the bootloader implementation.
Future Trends in Bootloader Technology
As embedded systems continue to evolve, so does bootloader technology. Future trends in bootloader development focus on enhancing functionality, improving security, and optimizing performance. Concepts like over-the-air (OTA) updates, secure boot mechanisms, and modular bootloader designs are shaping the future of embedded systems. This section delves into emerging trends in bootloader technology and their impact on the next generation of embedded systems.
By exploring the intricacies of bootloader fundamentals, developers can gain a comprehensive understanding of its significance in embedded systems design and operation. From defining its functions to addressing security concerns and exploring future trends, this blog section provides valuable insights into the world of bootloader development and its evolving role in the embedded systems landscape.
Significance of Robust Bootloaders
Ensuring System Integrity and Security
In the realm of embedded systems and IoT devices, robust bootloaders play a crucial role in ensuring the integrity and security of the system. By verifying the authenticity and integrity of the firmware before allowing it to boot, a secure bootloader can prevent unauthorized or malicious code from executing on the device. This verification process often involves cryptographic checks to ensure that only trusted firmware is loaded, thus protecting the system from potential security breaches and unauthorized access.
Avoiding Bricking Devices with Faulty Updates
A robust bootloader acts as a safety net when applying firmware updates. In case of a failed update or a corrupt firmware image, a reliable bootloader can detect the issue and prevent the device from becoming unusable. By implementing mechanisms such as rollback procedures or dual-image setups, a robust bootloader can help in recovering from failed updates, thereby avoiding situations where the device is rendered inoperable due to a faulty update process.
Enabling Seamless Firmware Updates
With the rise of IoT devices, the ability to perform seamless firmware updates is crucial for ensuring optimal performance and addressing security vulnerabilities. A robust bootloader simplifies the update process by managing the installation of new firmware versions efficiently and reliably without risking the device’s functionality. Additionally, features like secure boot and secure firmware updates further enhance the overall security posture of the system, ensuring that only authenticated updates are installed, thus reducing the risk of potential exploits or attacks.
Enhancing System Resilience and Recovery
Apart from ensuring system integrity and security, robust bootloaders also play a vital role in enhancing system resilience and recovery capabilities. By providing mechanisms for recovery in case of system failures or unexpected errors, bootloaders enable devices to recover from critical issues, reducing the impact of downtime and improving overall system reliability. Features like error detection, recovery modes, and fail-safe mechanisms contribute to maintaining system availability and minimizing disruptions in operation.
The significance of robust bootloaders cannot be overstated in the realm of embedded systems and IoT devices. From safeguarding system integrity and security to enabling seamless firmware updates and enhancing system resilience, a reliable bootloader is a cornerstone of a successful and secure device deployment. By incorporating robust bootloader solutions in device designs, developers can ensure that their products are equipped to handle evolving security threats, maintain operational continuity, and deliver a seamless user experience.
Design Strategies for Reliable Firmware Updates
The ability to update firmware remotely and reliably is crucial for ensuring the security and functionality of connected devices. This blog section will explore key design strategies for implementing reliable firmware updates.
Implementing Over-the-Air (OTA) Update Capabilities
One of the most efficient ways to update firmware on devices is through Over-the-Air (OTA) updates. This method allows devices to download and install firmware updates without requiring physical access. Implementing secure OTA update capabilities involves encryption, authentication, and error checking mechanisms to ensure the integrity and security of the update process.
Utilizing Dual Image Updates for Fail-Safe Operations
Dual image updates involve having two separate firmware images stored on a device, with one serving as the active image and the other as a backup. When a new firmware update is received, it is installed on the inactive image. This allows for a fail-safe mechanism where the device can revert to the previous firmware version in case the update fails or causes issues. By switching between the active and backup images, devices can ensure continuous operation even during the update process.
Integrating Rollback Mechanisms for Recovery
Rollback mechanisms are essential for quickly recovering from failed firmware updates. By providing a way to revert to a known good firmware version, devices can mitigate the impact of update failures and restore functionality promptly. Rollback mechanisms should be carefully designed to prevent potential security vulnerabilities that may arise from reverting to older firmware versions.
Ensuring Data Integrity during Updates
Maintaining data integrity during firmware updates is critical to prevent corruption or unauthorized modifications. Implementing cryptographic checksums or digital signatures can help verify the authenticity and integrity of the firmware files before installation. By confirming the integrity of the update packages, devices can reduce the risk of deploying faulty or malicious firmware.
Monitoring Update Progress and Health
Incorporating monitoring capabilities into the update process allows for real-time tracking of update progress and system health. By collecting metrics such as update completion status, error logs, and system performance during updates, device manufacturers can identify and address issues promptly. Monitoring update health enables proactive maintenance and troubleshooting, ensuring a smooth update experience for users.
By implementing these comprehensive design strategies for reliable firmware updates, device manufacturers can not only enhance the security, reliability, and efficiency of their update processes but also establish a foundation for future scalability and innovation in connected devices. Embracing a holistic approach to firmware updates ensures that devices remain resilient and adaptable in the face of evolving threats and technological advancements, ultimately delivering a seamless and secure user experience.
Ensuring Bootloader Security
Bootloaders play a critical role in the system startup process by loading the operating system into memory. However, they are prime targets for cyber attackers due to their privileged position in the boot process. In this section, we will explore the essential measures to fortify bootloader security and safeguard the integrity of the system.
Securing Bootloader Code and Communication
• Code Integrity Checks: Conducting regular integrity checks on the bootloader code helps ensure that it has not been tampered with. This can be achieved by implementing mechanisms like checksum verification or digital signatures.
• Secure Communication Protocols: Employing secure communication protocols such as HTTPS or TLS for bootloader communication enhances data confidentiality and mitigates the risk of eavesdropping or man-in-the-middle attacks.
Preventing Unauthorized Access and Tampering
• Multi-factor Authentication: Implementing multi-factor authentication, including something the user knows (password) and something the user has (token), adds an extra layer of security to prevent unauthorized access to the bootloader.
• Hardware Security Modules (HSMs): Utilizing HSMs for storing encryption keys and sensitive data provides a hardware-based root of trust, making it significantly harder for attackers to compromise the bootloader.
Implementing Secure Boot Processes
• Secure Boot Policy Enforcement: Enforcing strict policies for bootloader execution ensures that only trusted code is permitted to run, reducing the attack surface for potential threats.
• Remote Attestation: Incorporating remote attestation mechanisms allows external entities to verify the integrity of the bootloader and attest to its trustworthiness, enhancing overall system security.
Continuous Monitoring and Updates
• Security Patch Management: Regularly updating the bootloader with the latest security patches and fixes helps address known vulnerabilities and strengthens the overall resilience of the system.
• Security Event Logging: Maintaining detailed logs of bootloader activities and security events enables quick detection of anomalies or suspicious behavior, facilitating timely incident response.
Developers and system administrators face a constant challenge in ensuring the security of bootloaders, as any compromise at this critical stage can have severe consequences for the entire system. Cybersecurity threats continue to evolve, necessitating a proactive approach to secure bootloader design and implementation.
One crucial aspect of securing bootloaders is to consider the physical security of the device. Physical access to a device can potentially compromise its bootloader, leading to unauthorized access or tampering. Therefore, developers should implement tamper-resistant hardware and mechanisms to prevent unauthorized physical access.
Additionally, the secure storage of cryptographic keys is paramount for maintaining the integrity of the bootloader. Utilizing secure key storage solutions, such as Trusted Platform Modules (TPM) or Secure Elements, can help protect sensitive information and prevent key extraction attacks.
Furthermore, the adoption of secure coding practices and regular security audits can help identify and mitigate vulnerabilities in the bootloader code. Conducting security assessments, such as penetration testing and code reviews, can uncover potential weaknesses and ensure that the bootloader adheres to best security practices.
Safeguarding the bootloader is essential for establishing a strong security foundation in embedded systems. By implementing a comprehensive security strategy that encompasses secure coding practices, physical security measures, and continuous monitoring, developers can enhance the resilience of bootloaders against evolving cyber threats and ensure the overall security of embedded devices.
Testing and Validation Best Practices
Conducting Thorough Simulation Testing
Simulation testing is a critical aspect of the software development lifecycle. It involves creating simulated environments that replicate real-world scenarios to evaluate the system’s behavior under different conditions. By subjecting the system to a variety of simulated scenarios, developers can identify potential issues early on, allowing for timely resolutions and improved overall quality.
Performing Rigorous Integration Testing
Integration testing plays a vital role in ensuring the seamless operation of a software system. This testing phase focuses on verifying the interactions between various components or modules to validate their integration and functionality as a whole. Through rigorous integration testing, developers can detect and address any inconsistencies or compatibility issues, ultimately enhancing the reliability and performance of the system.
Incorporating Field Testing Feedback for Enhancements
Field testing is an invaluable method for gathering real-world feedback from end-users on the software’s performance and usability. By deploying the system in actual operational environments, developers can collect valuable insights that may not have been apparent during earlier testing phases. Analyzing and incorporating field testing feedback into the development process enables teams to make targeted enhancements that address user needs and improve overall satisfaction.
Continuous Improvement and Iterative Testing
In addition to the aforementioned best practices, embracing a culture of continuous improvement and iterative testing is essential for delivering high-quality software products. By regularly evaluating and refining testing strategies, teams can adapt to changing requirements, technologies, and user expectations. This iterative approach not only enhances the effectiveness of testing efforts but also fosters innovation and agility within the development process.
Automation and Test-driven Development
Automation tools and test-driven development methodologies are instrumental in streamlining testing processes and ensuring comprehensive test coverage. By automating repetitive tasks and incorporating testing early in the development cycle, teams can identify issues quickly, reduce manual errors, and expedite the delivery of reliable software solutions.
Conclusion
Adhering to testing and validation best practices is paramount for achieving successful software outcomes. By implementing thorough simulation testing, rigorous integration testing, and leveraging field testing feedback, developers can enhance product quality, user satisfaction, and overall project success. Embracing continuous improvement, automation, and test-driven development further strengthens testing efforts, enabling teams to deliver robust and innovative software solutions that meet the evolving demands of today’s digital landscape.
Addressing Challenges in Bootloader Design
Bootloaders play a critical role in the initialization process of computing devices, acting as the primary program that kickstarts the system and loads the operating system. However, the task of creating a secure and efficient bootloader is not without its challenges. This blog section will delve into the pivotal hurdles encountered in bootloader design and present effective strategies to conquer them.
Overcoming Security Vulnerabilities and Exploits
Protecting the integrity of the bootloader is paramount due to the potential catastrophic consequences of security breaches at this stage. We will delve deeper into prevalent security threats faced by bootloaders and explore advanced methodologies like secure boot protocols, robust cryptographic verification mechanisms, stringent code signing practices, and the importance of secure boot keys management to fortify the bootloader against exploitation.
Managing Resource Constraints for Optimal Operation
Bootloaders typically function within stringent resource limitations, necessitating designers to strike a delicate balance between minimizing code size and memory usage while upholding essential functionalities. This section will elucidate various optimization techniques for efficient bootloader design, encompassing strategies such as bootloader compression algorithms, selective feature incorporation, sophisticated memory management schemes, and the utilization of bootloader recovery mechanisms for fault tolerance.
Ensuring Seamless Compatibility Across Firmware Versions
The harmonious coexistence of the bootloader with diverse firmware iterations is imperative to avert system malfunctions and device incapacitation. Emphasizing the significance of version compatibility in bootloader architecture, we will explore innovative approaches to facilitate seamless updates, ensure backward compatibility through version negotiation protocols, and employ secure update mechanisms like firmware encryption to avoid potential system instabilities.
By confronting these challenges proactively, designers can craft resilient and dependable bootloaders that lay a robust groundwork for secure and streamlined system functionality. Upholding the integrity and efficiency of the bootloader is fundamental to safeguarding the overall system’s performance, resilience against external threats, and ensuring a smooth user experience.
Future Trends and Innovations in Bootloader Technology
In the rapidly advancing realm of technology, the significance of bootloader technology in the initialization process of electronic devices cannot be overstated. The future of bootloader technology is poised for remarkable transformations, driven by cutting-edge innovations and emerging trends that promise to redefine device initialization procedures.
AI Integration for Adaptive Bootloaders: Revolutionizing Initialization
The incorporation of Artificial Intelligence (AI) into bootloaders is heralding a new era of intelligent device initialization. By leveraging AI algorithms, adaptive bootloaders can dynamically adjust boot parameters based on real-time data analytics, user preferences, and usage patterns. This groundbreaking approach not only accelerates boot times but also optimizes system performance, leading to enhanced user experiences and operational efficiency.
Advancements in Secure Bootloader Protocols: Safeguarding Device Integrity
Amid escalating cybersecurity threats, the evolution of secure bootloader protocols plays a pivotal role in fortifying device integrity. The adoption of cutting-edge encryption methods, multifactor authentication, and secure boot processes ensures that devices are shielded against malicious attacks and unauthorized access attempts. By establishing a robust security framework during bootup, manufacturers can instill confidence in users regarding the safety and reliability of their devices.
Enhancements in Over-the-Air (OTA) Update Mechanisms: Enabling Seamless Updates
The refinement of Over-the-Air (OTA) update mechanisms is essential for facilitating hassle-free software updates and patch deployments. Recent innovations in bootloader technology have revolutionized the OTA process by introducing secure, efficient, and reliable update channels. This enables users to receive timely updates without disruption, ensuring that devices remain up-to-date with the latest features and security enhancements.
Energy-Efficient Bootloaders for Sustainable Devices
As sustainability gains prominence in the tech industry, energy-efficient bootloaders are emerging as a crucial innovation. By optimizing power consumption during the bootup phase, these eco-friendly bootloaders contribute to the overall energy efficiency of devices, prolonging battery life and reducing environmental impact. This focus on sustainability aligns with the growing demand for eco-conscious technology solutions in the market.
Looking ahead, the amalgamation of AI-driven adaptability, robust security measures, efficient update mechanisms, and sustainability initiatives is poised to shape the future landscape of bootloader technology. Embracing these transformative trends will not only enhance device performance and security but also pave the way for a more sustainable and user-centric technological ecosystem.
Designing Robust Bootloaders: Ensuring Reliable Firmware Updates
Designing robust bootloaders is imperative for ensuring reliable firmware updates in embedded systems. A well-designed bootloader plays a critical role in the system’s security, stability, and overall performance by facilitating safe and efficient firmware updates. By incorporating best practices, such as implementing secure boot mechanisms, error handling, and verification protocols, developers can enhance the resilience of their bootloaders and mitigate the risk of potential vulnerabilities. Ultimately, investing time and effort into designing robust bootloaders is essential for maintaining the integrity and functionality of embedded devices in today’s interconnected world.