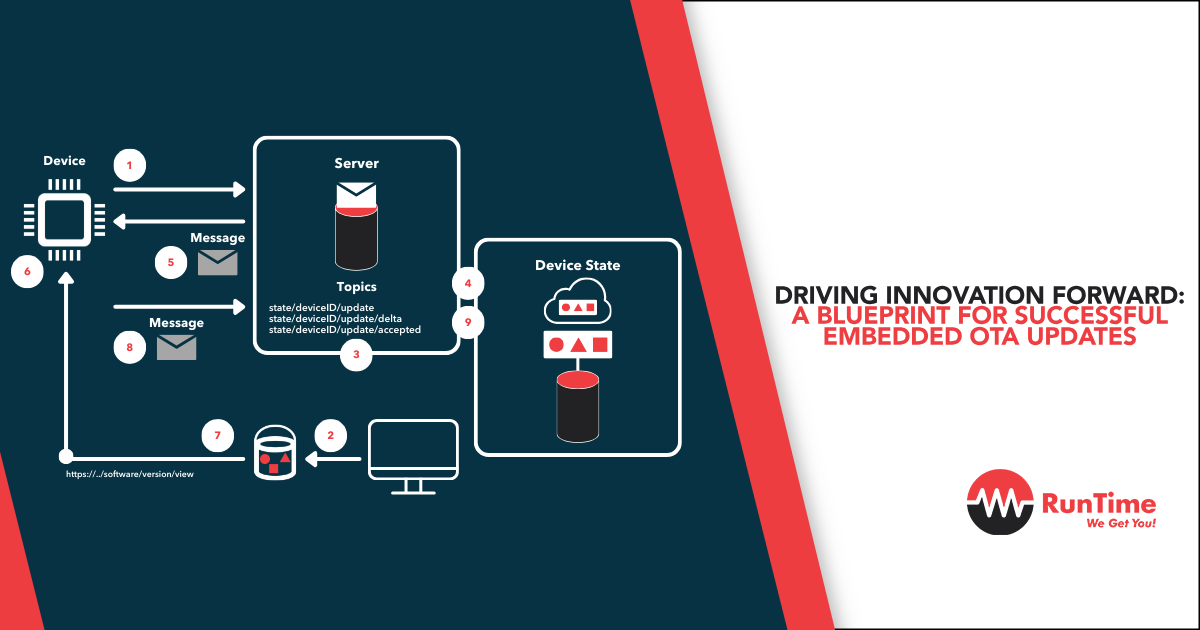
In the world of embedded systems, Over-the-Air (OTA) updates are crucial. They enable remote software updates, ensuring devices stay up-to-date and secure. With the rapid pace of technological advancement, the ability to update devices remotely is a game-changer. It saves time and resources while reducing the risks associated with manual updates. In short, OTA updates are a vital component of a successful embedded system strategy.
OTA updates not only keep devices secure and functional but also drive innovation. By allowing for continuous improvement, they enable companies to stay competitive in the market. Firmware updates can introduce new features, optimize performance, and fix bugs. This constant evolution keeps products fresh and relevant, meeting customer expectations and preventing obsolescence. Moreover, OTA updates create a feedback loop between developers and end-users, fostering a culture of innovation and responsiveness to customer needs.
This blog post will provide a comprehensive blueprint for implementing successful embedded OTA updates. The blueprint covers the basics of embedded OTA updates, the building blocks of a robust update system, designing an efficient update process, best practices, and case studies. By following this blueprint, businesses can harness the power of OTA updates to drive innovation and stay ahead of the competition.
Understanding the Basics of Embedded OTA Updates
Over-the-Air (OTA) updates refer to the wireless transmission of data, typically for the purpose of remotely updating software and firmware on devices. Embedded systems are specialized computer systems designed to perform specific tasks within larger electronic systems, such as automotive control units, medical devices, and industrial equipment.
When combined, embedded OTA updates provide a means to remotely update the software running on embedded devices. This functionality is crucial in maintaining device performance, security, and user experience.
Advantages and Disadvantages of OTA Updates for Embedded Systems
OTA updates offer numerous benefits for embedded systems. Some key advantages include:
- Reduced downtime: Remote updates minimize device downtime, as there’s no need for manual intervention.
- Cost savings: Eliminating the need for physical updates reduces labor and shipping costs.
- Improved security: Regular updates help address security vulnerabilities and protect devices from potential threats.
- Enhanced user experience: With the ability to introduce new features and fix bugs, OTA updates can greatly improve the end-user experience.
However, there are also some disadvantages to consider:
- Reliability concerns: Connectivity and update failures can potentially render a device inoperable.
- Security risks: An insecure update process may expose devices to cyberattacks and data breaches.
- Compatibility issues: Updates must be carefully designed to ensure compatibility with existing hardware and software components.
Key Factors to Consider When Designing an OTA Update Strategy
When creating an OTA update strategy for embedded systems, several key factors must be considered:
- Security: Implementing robust encryption and authentication measures is critical to ensure the integrity and confidentiality of updates.
- Reliability: Updates must be thoroughly tested to minimize the risk of device failures and unintended consequences.
- Efficiency: An efficient update distribution system is necessary to minimize bandwidth consumption and device downtime during updates.
- User experience: Balancing the frequency of updates with user convenience and device performance is essential to maintain a positive user experience.
- Scalability: The update system should be designed to handle future growth in device deployments and software complexity.
By carefully considering these factors, businesses can develop a successful embedded OTA update strategy that drives innovation and ensures long-term competitiveness.
The Building Blocks of a Robust Embedded OTA Update System
Secure and Reliable Connectivity
Importance of Secure Communication Channels
Secure communication channels are crucial for OTA updates. They protect against data interception, tampering, and unauthorized access. Implementing robust encryption and authentication measures, such as TLS/SSL and digital certificates, ensures the confidentiality, integrity, and authenticity of updates. In turn, this helps maintain device security and user trust.
Ensuring the Reliability of Connectivity
Reliable connectivity is another essential component of a robust OTA update system. Devices must maintain stable connections to receive updates. Factors such as network congestion, signal interference, and device power constraints can impact connectivity. To mitigate these challenges, businesses should consider implementing adaptive update algorithms, network performance monitoring, and device health checks.
Efficient Update Distribution
Update Servers and Cloud-Based Solutions
Efficient update distribution is vital to minimize bandwidth consumption, device downtime, and update delivery times. Update servers and cloud-based solutions can help achieve this by providing centralized, scalable, and cost-effective update distribution. Implementing edge computing, data compression techniques, and delta updates can further optimize update delivery and reduce bandwidth requirements.
The Role of Device Management Platforms
Device management platforms play a key role in streamlining the distribution and management of OTA updates. These platforms enable businesses to monitor and control devices remotely, schedule updates, and gather device data. Additionally, device management platforms can help automate update deployment processes, ensuring a timely and consistent rollout of updates across all devices.
Update Validation and Rollback Mechanisms
Ensuring Update Integrity and Authenticity
OTA updates must be validated to ensure their integrity and authenticity. This process typically involves verifying digital signatures and cryptographic hashes. Validation checks help confirm that updates originate from a trusted source and have not been tampered with during transmission. Implementing a robust validation process is critical to maintaining device security and user trust.
Implementing a Safe Rollback Process in Case of Errors
Despite thorough testing and validation, OTA updates can sometimes cause issues with device functionality. Implementing a safe rollback process can help mitigate the impact of such errors. A rollback mechanism enables devices to revert to a previous, stable software version in the event of an update failure. This ensures minimal disruption to device operations and end-user experience.
Designing an Efficient OTA Update Process
Understanding the Update Cycle
Planning and Scheduling Updates
Proper planning and scheduling are essential for a smooth OTA update process. Businesses should consider factors such as update frequency, device compatibility, and user convenience when planning updates. Scheduling updates during off-peak hours or allowing users to choose their preferred update times can help minimize disruptions and improve the overall user experience.
Ensuring Minimal Downtime During Updates
Minimizing device downtime during OTA updates is critical to maintain user satisfaction and device performance. Techniques such as delta updates, which only transmit changes to the software, can reduce update sizes and consequently, the time required for updates. Additionally, leveraging edge computing and local caching can help speed up update delivery and minimize network latency.
Testing and Deployment Strategies
Importance of Thorough Testing in a Controlled Environment
Thorough testing of OTA updates in a controlled environment is crucial to ensure their reliability and compatibility with existing devices. Testing should cover various aspects, including update functionality, security, and performance. By conducting comprehensive testing, businesses can identify and address potential issues before deploying updates to live devices, reducing the risk of update failures and negative user experiences.
Deploying Updates in Stages to Minimize Risks
Staged deployment of OTA updates can help minimize risks associated with software rollouts. By releasing updates to a small subset of devices initially, businesses can monitor their performance, gather user feedback, and identify potential issues before deploying updates more widely. This approach allows for quick identification and resolution of problems, minimizing the impact on users and device performance.
Tracking and Monitoring Update Success
Gathering Feedback from Devices Post-Update
Collecting feedback from devices after an OTA update is vital to gauge the update’s success and identify areas for improvement. This feedback can include device performance metrics, error logs, and user-reported issues. By analyzing this data, businesses can make informed decisions about future updates and continuously improve the update process.
Analyzing Update Data for Continuous Improvement
By analyzing the data gathered from devices post-update, businesses can identify trends, patterns, and potential issues in the update process. This information can be used to drive continuous improvement in the OTA update strategy, enhancing update efficiency, reliability, and user experience. Regular analysis of update data helps businesses stay agile and responsive to changing requirements and maintain a competitive edge in the market.
Best Practices for Implementing Embedded OTA Updates
Ensuring a Strong Security Foundation
Encryption and Authentication Methods
Implementing robust encryption and authentication methods is crucial for ensuring the security of OTA updates. Techniques such as SSL/TLS encryption and digital certificates help protect the confidentiality and integrity of update data. Additionally, strong authentication mechanisms, like public key infrastructure (PKI) and two-factor authentication (2FA), can help verify the authenticity of updates and protect against unauthorized access.
Protecting Against Common Security Threats
Businesses should be aware of common security threats related to OTA updates, such as man-in-the-middle attacks, spoofing, and data tampering. By implementing security best practices, like secure boot, hardware security modules (HSMs), and regular security audits, businesses can mitigate the risks associated with these threats and ensure the security of their OTA update process.
Planning for Update Compatibility and Scalability
Ensuring Updates are Compatible with Existing Devices
Compatibility is a critical aspect of a successful OTA update strategy. Businesses should carefully design updates to ensure they work seamlessly with existing hardware and software components. This may involve thorough testing, backward compatibility checks, and maintaining detailed documentation of device configurations and dependencies.
Designing Updates to Scale with Future Growth
As businesses grow and their device deployments expand, the OTA update process must be able to scale accordingly. Designing updates with scalability in mind ensures that the update infrastructure can handle increased demand and complexity without compromising efficiency or reliability. This can be achieved through the adoption of cloud-based solutions, edge computing, and modular update designs.
Maintaining a Focus on the End-User Experience
Balancing Update Frequency with User Convenience
While regular updates are essential for maintaining device security and performance, businesses must balance update frequency with user convenience. Excessive updates can disrupt user experience and lead to dissatisfaction. By carefully scheduling updates and considering user preferences, businesses can strike the right balance between maintaining device performance and ensuring a positive user experience.
Communicating Effectively with Users about Updates
Effective communication with users about OTA updates is vital for building trust and maintaining user satisfaction. Businesses should inform users about the purpose, benefits, and potential risks of updates, as well as provide clear instructions on how to initiate or postpone updates. By maintaining open lines of communication, businesses can address user concerns, gather feedback, and continuously improve their OTA update process.
Case Studies: Successful Embedded OTA Update Implementations
Example 1: Automotive Industry
How OTA Updates Have Revolutionized Vehicle Software Management
OTA updates have significantly transformed the way vehicle software is managed. In the past, vehicle owners had to visit dealerships for software updates, resulting in increased costs, inconvenience, and downtime. With OTA updates, automakers can now remotely update vehicle software, improving safety, performance, and user experience. This has led to a more streamlined and efficient software management process, with reduced costs and increased customer satisfaction.
Lessons Learned from Successful Automotive OTA Update Implementations
Successful automotive OTA update implementations have demonstrated the importance of strong security measures, thorough testing, and effective communication with users. By ensuring the integrity and reliability of updates, automakers can build trust with vehicle owners and protect their brand reputation. Additionally, gathering user feedback and analyzing update data allows automakers to continuously improve their update process, further enhancing the end-user experience and driving innovation in the automotive industry.
Example 2: Industrial IoT Applications
Ensuring the Reliability and Security of Connected Industrial Devices
As Industrial IoT applications grow in complexity and scale, ensuring the reliability and security of connected devices is paramount. OTA updates play a critical role in maintaining the performance, stability, and security of these devices. By implementing robust encryption, authentication, and rollback mechanisms, businesses can protect their industrial devices from potential threats and minimize the risks associated with software updates.
Best Practices for Implementing OTA Updates in the Industrial Sector
Key best practices for implementing OTA updates in the industrial sector include thorough testing in controlled environments, staged deployment, and continuous monitoring of update success. These practices help minimize the risks associated with software updates, ensuring the stability and security of connected industrial devices. By adopting these best practices, businesses can effectively harness the power of OTA updates to drive innovation and maintain a competitive edge in the Industrial IoT landscape.
Conclusion
Embedded OTA updates play a crucial role in driving innovation, ensuring device security, and maintaining a competitive edge in the market. By enabling businesses to remotely update software, OTA updates facilitate continuous improvement and a strong feedback loop between developers and end-users. As a result, products stay fresh, relevant, and secure, meeting customer expectations and preventing obsolescence.
Businesses are encouraged to adopt a strategic approach to implementing OTA updates. By considering factors such as security, reliability, efficiency, user experience, and scalability, businesses can develop a successful OTA update strategy that meets their unique requirements. Following the best practices and lessons learned from successful implementations can further enhance the effectiveness of an embedded OTA update system.
If you need assistance in implementing a robust and efficient embedded OTA update system, our team of experts is here to help. With our technical expertise and experience, we can guide you through the process and ensure a successful implementation that drives innovation and keeps your devices secure. Don’t hesitate to reach out and leverage our knowledge to stay ahead in the rapidly evolving world of embedded systems and IoT.
Hire Highly-Skilled Engineers with RunTime Recruitment
Our expert team of engineers-turned-recruiters offers in-depth knowledge of technical recruiting in the engineering industry.
If your company is looking to recruit highly-skilled engineers worldwide, contact us today and we will do the sourcing for you. Or if you’re an engineer looking for new opportunities, you can check RunTime Recruitment’s job site for job vacancies.